Frequently Asked Questions

Quick Start
To get started with Forward Email:
-
Create an account at forwardemail.net/register
-
Add and verify your domain under My Account → Domains
-
Add and configure email aliases/mailboxes under My Account → Domains → Aliases
-
Test your setup by sending an email to one of your new aliases
Tip
DNS changes can take up to 24-48 hours to propagate globally, though they often take effect much sooner.
Introduction
What is Forward Email
Note
Forward Email is perfect for individuals, small businesses, and developers who want professional email addresses without the cost and maintenance of a full email hosting solution.
Forward Email is a fully featured email service provider and email hosting provider for custom domain names.
It's the only free and open-source service, and lets you use custom domain email addresses without the complexity of setting up and maintaining your own email server.
Our service forwards emails sent to your custom domain to your existing email account – and you can even use us as your dedicated email hosting provider.
Key features of Forward Email:
- Custom Domain Email: Use professional email addresses with your own domain name
- Free Tier: Basic email forwarding at no cost
- Enhanced Privacy: We don't read your emails or sell your data
- Open Source: Our entire codebase is available on GitHub
- SMTP, IMAP, and POP3 Support: Full email sending and receiving capabilities
- End-to-End Encryption: Support for OpenPGP/MIME
- Custom Catch-All Aliases: Create unlimited email aliases
You can compare us to 56+ other email service providers on our Email Comparison page.
Tip
Learn more about Forward Email by reading our free Technical Whitepaper
Who uses Forward Email
We provide email hosting and email forwarding service to 500,000+ domains and these notable users:
| Customer | Case Study |
|---|---|
| U.S. Naval Academy | 📄 Case Study |
| Canonical | 📄 Case Study |
| Netflix Games | |
| The Linux Foundation | 📄 Case Study |
| The PHP Foundation | |
| Fox News Radio | |
| Disney Ad Sales | |
| jQuery | 📄 Case Study |
| LineageOS | |
| Ubuntu | 📄 Case Study |
| Kubuntu | 📄 Case Study |
| Lubuntu | 📄 Case Study |
| The University of Cambridge | 📄 Case Study |
| The University of Maryland | 📄 Case Study |
| The University of Washington | 📄 Case Study |
| Tufts University | 📄 Case Study |
| Swarthmore College | 📄 Case Study |
| Government of South Australia | |
| Government of Dominican Republic | |
| Fly.io | |
| RCD Hotels | |
| Isaac Z. Schlueter (npm) | 📄 Case Study |
| David Heinemeier Hansson (Ruby on Rails) |
What is Forward Email's history
You can learn more about Forward Email on our About page.
How fast is this service
Note
Our system is designed for speed and reliability, with multiple redundant servers to ensure your emails are delivered promptly.
Forward Email delivers messages with minimal delay, typically within seconds of receipt.
Performance metrics:
- Average Delivery Time: Less than 5-10 seconds from receipt to forwarding (see our Time to Inbox "TTI" monitoring page)
- Uptime: 99.9%+ service availability
- Global Infrastructure: Servers strategically located for optimal routing
- Automatic Scaling: Our system scales during peak email periods
We operate in real-time, unlike other providers which rely upon delayed queues.
We do not write to disk or store logs – with the exception of errors and outbound SMTP (see our Privacy Policy).
Everything is done in-memory and our source code is on GitHub.
Email Clients
Thunderbird
- Create a new alias and generate a password in your Forward Email dashboard
- Open Thunderbird and go to Edit → Account Settings → Account Actions → Add Mail Account
- Enter your name, Forward Email address, and password
- Click Configure manually and enter:
- Incoming: IMAP,
imap.forwardemail.net, port 993, SSL/TLS - Outgoing: SMTP,
smtp.forwardemail.net, port 587, STARTTLS
- Incoming: IMAP,
- Click Done
Microsoft Outlook
- Create a new alias and generate a password in your Forward Email dashboard
- Go to File → Add Account
- Enter your Forward Email address and click Connect
- Choose Advanced options and select Let me set up my account manually
- Select IMAP and enter:
- Incoming:
imap.forwardemail.net, port 993, SSL - Outgoing:
smtp.forwardemail.net, port 587, TLS - Username: Your full email address
- Password: Your generated password
- Incoming:
- Click Connect
Apple Mail
- Create a new alias and generate a password in your Forward Email dashboard
- Go to Mail → Preferences → Accounts → +
- Select Other Mail Account
- Enter your name, Forward Email address, and password
- For server settings, enter:
- Incoming:
imap.forwardemail.net - Outgoing:
smtp.forwardemail.net - Username: Your full email address
- Password: Your generated password
- Incoming:
- Click Sign In
eM Client
- Create a new alias and generate a password in your Forward Email dashboard
- Open eM Client and go to Menu → Accounts → + Add Account
- Click on Mail and then select Other
- Enter your Forward Email address and click Next
- Enter the following server settings:
- Incoming server:
imap.forwardemail.net - Outgoing server:
smtp.forwardemail.net
- Incoming server:
- Enter your full email address as the User name and your generated password as the Password for both incoming and outgoing servers.
- eM Client will test the connection. Once it passes, click Next.
- Enter your name and choose an account name.
- Click Finish.
Mobile Devices
For iOS:
- Go to Settings → Mail → Accounts → Add Account → Other
- Tap Add Mail Account and enter your details
- For server settings, use the same IMAP and SMTP settings as above
For Android:
- Go to Settings → Accounts → Add Account → Personal (IMAP)
- Enter your Forward Email address and password
- For server settings, use the same IMAP and SMTP settings as above
Sendmail SMTP Relay Configuration
You can configure Sendmail to relay emails through Forward Email's SMTP servers. This is a common setup for legacy systems or applications that rely on Sendmail.
Configuration
-
Edit your
sendmail.mcfile, typically located at/etc/mail/sendmail.mc:sudo nano /etc/mail/sendmail.mc -
Add the following lines to define the smart host and authentication:
define(`SMART_HOST', `smtp.forwardemail.net')dnl define(`RELAY_MAILER_ARGS', `TCP $h 587')dnl define(`confAUTH_MECHANISMS', `EXTERNAL GSSAPI DIGEST-MD5 CRAM-MD5 LOGIN PLAIN')dnl FEATURE(`authinfo',`hash -o /etc/mail/authinfo.db')dnl -
Create the authentication file
/etc/mail/authinfo:sudo nano /etc/mail/authinfo -
Add your Forward Email credentials to the
authinfofile:AuthInfo:smtp.forwardemail.net "U:your-alias@yourdomain.com" "P:your-generated-password" "M:PLAIN" -
Generate the authentication database and secure the files:
sudo makemap hash /etc/mail/authinfo < /etc/mail/authinfo sudo chmod 600 /etc/mail/authinfo /etc/mail/authinfo.db -
Rebuild the Sendmail configuration and restart the service:
sudo make -C /etc/mail sudo systemctl restart sendmail
Testing
Send a test email to verify the configuration:
echo "Test email from Sendmail" | mail -s "Sendmail Test" recipient@your-domain.your-domain.your-domain.your-domain.example.com
Exim4 SMTP Relay Configuration
Exim4 is a popular MTA on Debian-based systems. You can configure it to use Forward Email as a smarthost.
Configuration
-
Run the Exim4 configuration tool:
sudo dpkg-reconfigure exim4-config -
Select the following options:
- General type of mail configuration: mail sent by smarthost; received via SMTP or fetchmail
- System mail name: your.hostname
- IP-addresses to listen on for incoming SMTP connections: 127.0.0.1 ; ::1
- Other destinations for which mail is accepted: (leave blank)
- Domains to relay mail for: (leave blank)
- IP address or host name of the outgoing smarthost: smtp.forwardemail.net::587
- Hide local mail name in outgoing mail? No
- Keep number of DNS-queries minimal (Dial-on-Demand)? No
- Delivery method for local mail: Mbox format in /var/mail/
- Split configuration into small files? No
-
Edit the
passwd.clientfile to add your credentials:sudo nano /etc/exim4/passwd.client -
Add the following line:
smtp.forwardemail.net:your-alias@yourdomain.com:your-generated-password -
Update the configuration and restart Exim4:
sudo update-exim4.conf sudo systemctl restart exim4
Testing
Send a test email:
echo "Test from Exim4" | mail -s "Exim4 Test" recipient@your-domain.your-domain.your-domain.your-domain.example.com
msmtp SMTP Client Configuration
msmtp is a lightweight SMTP client that's useful for sending emails from scripts or command-line applications.
Configuration
-
Create or edit the msmtp configuration file at
~/.msmtprc:nano ~/.msmtprc -
Add the following configuration:
defaults auth on tls on tls_trust_file /etc/ssl/certs/ca-certificates.crt logfile ~/.msmtp.log account forwardemail host smtp.forwardemail.net port 587 from your-alias@yourdomain.com user your-alias@yourdomain.com password your-generated-password account default : forwardemail -
Set the correct permissions for the configuration file:
chmod 600 ~/.msmtprc
Testing
Send a test email:
echo "This is a test email from msmtp" | msmtp -a default recipient@your-domain.your-domain.your-domain.your-domain.example.com
Command-line Email Clients
Popular command-line email clients like Mutt, NeoMutt, and Alpine can be configured to use Forward Email's SMTP servers for sending mail. The configuration will be similar to the msmtp setup, where you provide the SMTP server details and your credentials in the respective configuration files (.muttrc, .neomuttrc, or .pinerc).
Windows Email Configuration
For Windows users, you can configure popular email clients like Microsoft Outlook and eM Client using the IMAP and SMTP settings provided in your Forward Email account. For command-line or scripting use, you can use PowerShell's Send-MailMessage cmdlet (though it is considered obsolete) or a lightweight SMTP relay tool like E-MailRelay.
Postfix SMTP Relay Configuration
You can configure Postfix to relay emails through Forward Email's SMTP servers. This is useful for server applications that need to send emails.
Installation
- Install Postfix on your server:
# Ubuntu/Debian
sudo apt update && sudo apt install postfix
# CentOS/RHEL
sudo yum install postfix
# macOS
brew install postfix
- During installation, select "Internet Site" when prompted for configuration type.
Configuration
- Edit the main Postfix configuration file:
sudo nano /etc/postfix/main.cf
- Add or modify these settings:
# SMTP relay configuration
relayhost = [smtp.forwardemail.net]:587
smtp_use_tls = yes
smtp_sasl_auth_enable = yes
smtp_sasl_password_maps = hash:/etc/postfix/sasl_passwd
smtp_sasl_security_options = noanonymous
smtp_tls_CAfile = /etc/ssl/certs/ca-certificates.crt
- Create the SASL password file:
sudo nano /etc/postfix/sasl_passwd
- Add your Forward Email credentials:
[smtp.forwardemail.net]:587 your-alias@yourdomain.com:your-generated-password
- Secure and hash the password file:
sudo chmod 600 /etc/postfix/sasl_passwd
sudo postmap /etc/postfix/sasl_passwd
- Restart Postfix:
sudo systemctl restart postfix
Testing
Test your configuration by sending a test email:
echo "Test email body" | mail -s "Test Subject" recipient@your-domain.your-domain.your-domain.your-domain.example.com
How to Send Mail As using Gmail
-
Go to My Account Domains Settings Outbound SMTP Configuration and follow setup instructions
-
Create a new alias for your domain under My Account Domains Aliases (e.g.
hello@your-domain.your-domain.your-domain.your-domain.example.com) -
Click on Generate Password next to the newly created alias. Copy to your clipboard and securely store the generated password shown on the screen.
-
Go to Gmail and under Settings Accounts and Import Send mail as, click "Add another email address"
-
When prompted for "Name", enter the name that you want your email to be seen as "From" (e.g. "Linus Torvalds").
-
When prompted for "Email address", enter the full email address of an alias you created under My Account Domains Aliases (e.g.
hello@your-domain.your-domain.your-domain.your-domain.example.com) -
Uncheck "Treat as an alias"
-
Click "Next Step" to proceed
-
When prompted for "SMTP Server", enter
smtp.forwardemail.netand leave the port as587 -
When prompted for "Username", enter the full email address of an alias you created under My Account Domains Aliases (e.g.
hello@your-domain.your-domain.your-domain.your-domain.example.com) -
When prompted for "Password", paste the password from Generate Password in step 3 above
-
Leave the radio button checked for "Secured connection using TLS"
-
Click "Add Account" to proceed
-
Open a new tab to Gmail and wait for your verification email to arrive (you will receive a verification code that confirms you are the owner of the email address you are attempting to "Send Mail As")
-
Once it arrives, copy and paste the verification code at the prompt you received in the previous step
-
Once you've done that, go back to the email and click the link to "confirm the request". You will most likely need to do this step and the previous step for the email to be correctly configured.
What is the legacy free guide for Send Mail As using Gmail
-
You need to have Gmail's Two-Factor Authentication enabled for this to work. Visit https://www.google.com/landing/2step/ if you do not have it enabled.
-
Once Two-Factor Authentication is enabled (or if you already had it enabled), then visit https://myaccount.google.com/apppasswords.
-
When prompted for "Select the app and device you want to generate the app password for":
- Select "Mail" under the drop-down for "Select app"
- Select "Other" under the drop-down for "Select device"
- When prompted for text input, enter your custom domain's email address you're forwarding from (e.g.
hello@your-domain.your-domain.your-domain.your-domain.example.com- this will help you keep track in case you use this service for multiple accounts)
-
Copy the password to your clipboard that is automatically generated
Important: If you are using G Suite, visit your admin panel Apps G Suite Settings for Gmail Settings and make sure to check "Allow users to send mail through an external SMTP server...". There will be some delay for this change to be activated, so please wait a few minutes. -
Go to Gmail and under Settings Accounts and Import Send mail as, click "Add another email address"
-
When prompted for "Name", enter the name that you want your email to be seen as "From" (e.g. "Linus Torvalds")
-
When prompted for "Email address", enter the email address with the custom domain you used above (e.g.
hello@your-domain.your-domain.your-domain.your-domain.example.com) -
Uncheck "Treat as an alias"
-
Click "Next Step" to proceed
-
When prompted for "SMTP Server", enter
smtp.gmail.comand leave the port as587 -
When prompted for "Username", enter the portion of your Gmail address without the gmail.com part (e.g. just "user" if my email is user@gmail.com)
Important: If the "Username" portion is autofilled, then you will need to change this to the username portion of your Gmail address instead. -
When prompted for "Password", paste from your clipboard the password you generated in step 2 above
-
Leave the radio button checked for "Secured connection using TLS"
-
Click "Add Account" to proceed
-
Open a new tab to Gmail and wait for your verification email to arrive (you will receive a verification code that confirms you are the owner of the email address you are attempting to "Send Mail As")
-
Once it arrives, copy and paste the verification code at the prompt you received in the previous step
-
Once you've done that, go back to the email and click the link to "confirm the request". You will most likely need to do this step and the previous step for the email to be correctly configured.
Advanced Gmail Routing Configuration
If you want to set up advanced routing in Gmail so that aliases that don't match a mailbox will forward to Forward Email's mail exchanges, follow these steps:
- Log in to your Google Admin console at admin.google.com
- Go to Apps → Google Workspace → Gmail → Routing
- Click on Add Route and configure the following settings:
Single Recipient Settings:
- Select "Change envelope recipient" and enter your primary Gmail address
- Check "Add X-Gm-Original-To header with original recipient"
Envelope Recipient Patterns:
- Add a pattern that matches all non-existent mailboxes (e.g.,
.*@yourdomain.com)
Email Server Settings:
- Select "Route to host" and enter
mx1.forwardemail.netas the primary server - Add
mx2.forwardemail.netas the backup server - Set port to 25
- Select "Require TLS" for security
- Click Save to create the route
Advanced Outlook Routing Configuration
For Microsoft 365 (formerly Office 365) users who want to set up advanced routing so that aliases that don't match a mailbox will forward to Forward Email's mail exchanges:
- Log in to the Microsoft 365 admin center at admin.microsoft.com
- Go to Exchange → Mail flow → Rules
- Click Add a rule and select Create a new rule
- Name your rule (e.g., "Forward non-existent mailboxes to Forward Email")
- Under Apply this rule if, select:
- "The recipient address matches..."
- Enter a pattern that matches all addresses at your domain (e.g.,
*@yourdomain.com)
- Under Do the following, select:
- "Redirect the message to..."
- Choose "The following mail server"
- Enter
mx1.forwardemail.netand port 25 - Add
mx2.forwardemail.netas a backup server
- Under Except if, select:
- "The recipient is..."
- Add all your existing mailboxes that should not be forwarded
- Set the rule priority to ensure it runs after other mail flow rules
- Click Save to activate the rule
Troubleshooting
Why am I not receiving my test emails
If you're sending a test email to yourself, then it may not show up in your inbox because it has the same "Message-ID" header.
This is a widely known issue, and also affects services such as Gmail. Here is the official Gmail answer regarding this issue.
If you continue to have issues, then it is most likely to be an issue with DNS propagation. You will need to wait a bit longer and try again (or try setting a lower TTL value on your TXT records).
Still having issues? Please contact us so we can help investigate the issue and find a quick resolution.
How do I configure my email client to work with Forward Email
| Type | Hostname | Protocol | Ports |
|---|---|---|---|
| IMAP | imap.forwardemail.net |
SSL/TLS Preferred | 993 and 2993 |
| SMTP | smtp.forwardemail.net |
SSL/TLS Preferred or TLS (STARTTLS) | 465 and 2465 for SSL/TLS (or) 587, 2587, 2525, and 25 for TLS (STARTTLS) |
Why are my emails landing in Spam and Junk and how can I check my domain reputation
This section guides you if your outbound mail is using our SMTP servers (e.g. smtp.forwardemail.net) (or forwarded via mx1.forwardemail.net or mx2.forwardemail.net) and it is being delivered in the Spam or Junk folder of recipients.
We routinely monitor our IP addresses against all reputable DNS denylists, therefore it is most likely a domain-reputation specific issue.
Emails can land in spam folders for several reasons:
-
Missing Authentication: Set up SPF, DKIM, and DMARC records.
-
Domain Reputation: New domains often have neutral reputation until they establish a sending history.
-
Content Triggers: Certain words or phrases can trigger spam filters.
-
Sending Patterns: Sudden increases in email volume can look suspicious.
You can try to use one or more of these tools to check your domain's reputation and categorization:
Reputation and Blocklist Check Tools
IP Removal Request Forms by Provider
If your IP address has been blocked by a specific email provider, use the appropriate removal form or contact below:
| Provider | Removal Form / Contact | Notes |
|---|---|---|
| Google/Gmail | https://support.google.com/mail/contact/bulk_send_new | Bulk sender contact form |
| Microsoft (Outlook/Office 365/Hotmail) | https://sender.office.com | Office 365 IP delist portal |
| Yahoo/AOL/Verizon | https://senders.yahooinc.com/ | Yahoo Sender Hub |
| Apple/iCloud | https://ipcheck.proofpoint.com/ | Apple uses Proofpoint for IP reputation |
| Proofpoint | https://ipcheck.proofpoint.com/ | Proofpoint IP check and removal |
| Barracuda Networks | https://www.barracudacentral.org/lookups/lookup-reputation | Barracuda reputation lookup and removal |
| Cloudmark | https://csi.cloudmark.com/en/reset/ | Cloudmark CSI reset request |
| GoDaddy/SecureServer | https://unblock.secureserver.net | GoDaddy IP unblock request form |
| Comcast/Xfinity | https://spa.xfinity.com/report | Comcast IP removal request |
| Charter/Spectrum | https://www.spectrum.net/support/internet/understanding-email-error-codes | Contact Spectrum support for removal |
| AT&T | abuse_rbl@abuse-att.net |
Email for removal request |
| Cox Communications | unblock.request@cox.net |
Email for removal request |
| CenturyLink/Lumen | abuse@centurylink.com |
Uses Cloudfilter |
| Windstream | abuse@windstream.net |
Email for removal request |
| t-online.de (Germany) | tobr@rx.t-online.de |
Email for removal request |
| Orange France | https://postmaster.orange.fr/ | Use contact form or email abuse@orange.fr |
| GMX | https://postmaster.gmx.net/en/contact | GMX postmaster contact form |
| Mail.ru | https://postmaster.mail.ru/ | Mail.ru postmaster portal |
| Yandex | https://postmaster.yandex.ru/ | Yandex postmaster portal |
| QQ Mail (Tencent) | https://open.mail.qq.com/ | QQ Mail whitelist application (Chinese) |
| Netease (163.com) | https://mail.163.com/postmaster/ | Netease postmaster portal |
| Alibaba/Aliyun/HiChina | https://www.alibabacloud.com/help/en/alibaba-mail/ | Contact via Alibaba Cloud console |
| Amazon SES | https://docs.aws.amazon.com/ses/latest/dg/faqs-dnsbls.html | AWS SES console > Blacklist Removal |
| SendGrid | https://support.sendgrid.com/ | Contact SendGrid support |
| Mimecast | https://community.mimecast.com/ | Uses third-party RBLs - contact specific RBL |
| Fastmail | https://www.fastmail.com/support/ | Contact Fastmail support |
| Zoho | https://help.zoho.com/portal/en/kb/campaigns/faqs/campaign-review/articles/how-do-i-delist-my-ip-address | Contact Zoho support |
| ProtonMail | https://proton.me/support/contact | Contact Proton support |
| Tutanota | https://tutanota.com/support | Contact Tutanota support |
| Hushmail | https://www.hushmail.com/support/ | Contact Hushmail support |
| Mailbox.org | https://mailbox.org/en/support | Contact Mailbox.org support |
| Posteo | https://posteo.de/en/site/contact | Contact Posteo support |
| DuckDuckGo Email | https://duckduckgo.com/email/support | Contact DuckDuckGo support |
| Sonic.net | https://www.sonic.com/support | Contact Sonic support |
| Telus | https://www.telus.com/en/support | Contact Telus support |
| Vodafone Germany | https://www.vodafone.de/hilfe/ | Contact Vodafone support |
| Xtra (Spark NZ) | https://www.spark.co.nz/help/ | Contact Spark NZ support |
| UOL/BOL (Brazil) | https://ajuda.uol.com.br/ | Contact UOL support (Portuguese) |
| Libero (Italy) | https://aiuto.libero.it/ | Contact Libero support (Italian) |
| Telenet (Belgium) | https://www2.telenet.be/en/support/ | Contact Telenet support |
| Facebook/WhatsApp | https://www.facebook.com/business/help | Contact Facebook business support |
| https://www.linkedin.com/help/linkedin | Contact LinkedIn support | |
| Groups.io | https://groups.io/helpcenter | Contact Groups.io support |
| Earthlink/Vade Secure | https://sendertool.vadesecure.com/en/ | Vade Secure sender tool |
| Cloudflare Email Security | https://www.cloudflare.com/products/zero-trust/email-security/ | Contact Cloudflare support |
| Hornetsecurity/Expurgate | https://www.hornetsecurity.com/ | Contact Hornetsecurity support |
| SpamExperts/Antispamcloud | https://www.spamexperts.com/ | Contact via hosting provider |
| Mail2World | https://www.mail2world.com/support/ | Contact Mail2World support |
Tip
Start with a low volume of high-quality emails to build a positive reputation before sending in larger volumes.
Important
If your domain is on a blacklist, each blacklist has its own removal process. Check their websites for instructions.
Tip
If you need additional help or find that we are false-positive listed as spam by a certain email service provider, then please contact us.
What should I do if I receive spam emails
You should unsubscribe from the emailing list (if possible) and block the sender.
Please do not report the message as spam, but instead forward it to our manually curated and privacy-focused abuse prevention system.
The email address to forward spam to is: abuse@forwardemail.net
Why are my test emails sent to myself in Gmail showing as "suspicious"
If you see this error message in Gmail when you send a test to yourself, or when a person you're emailing with your alias sees an email from you for the first time, then please do not worry – as this is a built-in safety feature of Gmail.
You can simply click "Looks safe". For example, if you were to send a test message using the send mail as feature (to someone else), then they will not see this message.
However if they do see this message, it's because they were normally used to seeing your emails come from john@gmail.com instead of john@customdomain.com (just an example). Gmail will alert the users just to make sure things are safe just in case, there is no workaround.
Can I remove the via forwardemail dot net in Gmail
This topic is related to a widely known issue in Gmail where extra info appears next to a sender's name.
As of May 2023 we support sending email with SMTP as an add-on for all paid users – which means that you can remove the via forwardemail dot net in Gmail.
Note that this FAQ topic is specific for those using the How to Send Mail As using Gmail feature.
Please see the section on Do you support sending email with SMTP for configuration instructions.
Data Management
Where are your servers located
Tip
We may soon announce our EU datacenter location hosted under forwardemail.eu. Subscribe to the discussion at https://github.com/orgs/forwardemail/discussions/336 for updates.
Our servers are located primarily in Denver, Colorado – see https://forwardemail.net/ips for our complete list of IP addresses.
You can learn about our subprocessors on our GDPR, DPA, and Privacy pages.
How do I export and backup my mailbox
At anytime you can export your mailboxes as EML, Mbox, or encrypted SQLite formats.
Go to My Account Domains Aliases Download Backup and select your preferred export format type.
You will be emailed a link to download the export once it has finished.
Note that this export download link expires after 4 hours for security concerns.
If you need to inspect your exported EML or Mbox formats, then these open-soruce tools may be useful:
| Name | Format | Platform | GitHub URL |
|---|---|---|---|
| MBox Viewer | Mbox | Windows | https://github.com/eneam/mboxviewer |
| mbox-web-viewer | Mbox | All platforms | https://github.com/PHMRanger/mbox-web-viewer |
| EmlReader | EML | Windows | https://github.com/ayamadori/EmlReader |
| Email viewer | EML | VSCode | https://github.com/joelharkes/vscode_email_viewer |
| eml-reader | EML | All platforms | https://github.com/s0ph1e/eml-reader |
Additionally if you need to convert a Mbox file to EML file, then you can use https://github.com/noelmartinon/mboxzilla.
How do I import and migrate my existing mailbox
You can easily import your email to Forward Email (e.g. using Thunderbird) with the instructions below:
-
Export your email from your existing email provider:
Email Provider Export Format Export Instructions Gmail MBOX https://takeout.google.com/settings/takeout/custom/gmail Outlook PST Tip: If you are using Outlook (PST export format), then you could simply follow the instructions under "Other" below. However we have provided links below to convert PST to MBOX/EML format based off your operating system:- Zinkuba for Windows (GitHub)
- readpst for Windows cygwin – (e.g.
readpst -u -o $OUT_DIR $IN_DIRreplacing$OUT_DIRand$IN_DIRwith the output directory and input directory paths respectively). - readpst for Ubuntu/Linux – (e.g.
sudo apt-get install readpstand thenreadpst -u -o $OUT_DIR $IN_DIR, replacing$OUT_DIRand$IN_DIRwith the output directory and input directory paths respectively). - readpst for macOS (via brew) – (e.g.
brew install libpstand thenreadpst -u -o $OUT_DIR $IN_DIR, replacing$OUT_DIRand$IN_DIRwith the output directory and input directory paths respectively). - PST Converter for Windows (GitHub)
Apple Mail MBOX https://support.apple.com/guide/mail/import-or-export-mailboxes-mlhlp1030/mac#apd37a3190755974 Fastmail EML https://www.fastmail.help/hc/en-us/articles/360060590573-Download-all-your-data#downloadmail Proton Mail MBOX/EML https://proton.me/support/export-emails-import-export-app Tutanota EML https://github.com/crepererum-oss/tatutanatata Gandi EML https://docs.gandi.net/en/gandimail/common_operations/backup_email.html#contents Zoho EML https://www.zoho.com/mail/help/import-export-emails.html#alink2 Other Use Thunderbird Set up your existing email account in Thunderbird and then use the ImportExportTools NG plugin to export and import your email. You may also be able to simply copy/paste or drag/drop emails between one account to another. -
Download, install, and open Thunderbird.
-
Create a new account using your alias' full email address (e.g.
you@yourdomain.com) and your generated password. If you do not yet have a generated password, then refer to our setup instructions. -
Download and install the ImportExportTools NG Thunderbird plugin.
-
Create a new local folder in Thunderbird, and then right click on it → select the
ImportExportTools NGoption → chooseImport mbox file(for MBOX export format) – or –Import messages/Import all messages from a directory(for EML export format). -
Drag/drop from the local folder to a new (or existing) IMAP folder in Thunderbird you wish to upload messages to in IMAP storage with our service. This will ensure they are backed up online with our SQLite encrypted storage.
Tip: If you are confused as to how to import into Thunderbird, then you can refer to official instructions at https://kb.mozillazine.org/Importing_folders and https://github.com/thunderbird/import-export-tools-ng/wiki.
Do you support self-hosting
Yes, as of March 2025, we support a self-hosted option. Read the blog here. Checkout the self-hosted guide to get started. And for those interested in a more broken down step-by-step version see our Ubuntu or Debian based guides.
Email Configuration
How do I get started and set up email forwarding
user@gmail.com with the email address you want to forward emails to (if it isn't already accurate). Similarly be sure to replace your-domain.your-domain.your-domain.your-domain.example.com with your custom domain name (if it isn't already accurate).
- If you have already registered your domain name somewhere, then you must completely skip this step and go to step two! Otherwise you can click here to register your domain name.
-
Do you remember where you registered your domain? Once you remember this, then follow the instructions below:
Important: You must open a new tab and sign in to your domain registrar. You can easily click on your "Registrar" below to automatically do this. In this new tab, you must navigate to the DNS management page at your registrar – and we have provided the step by step navigation steps below under the "Steps to Configure" column. Once you've navigated to this page in the new tab, you can return to this tab and proceed to step three below. Do not close the opened tab yet; you will need it for future steps!
Registrar Steps to Configure 1&1 Log in Domain Center (Select your domain) Edit DNS Settings Amazon Route 53 Log in Hosted Zones (Select your domain) Aplus.net Log in My Servers Domain Management DNS Manager Bluehost FOR ROCK: Log in Domains (Click the ▼ icon next to manage) DNS
FOR LEGACY: Log in Domains Zone editor (Select your domain)Cloudflare Log in DNS DNS Made Easy Log in DNS (Select your domain) DNSimple Log in (Select your domain) DNS Manage Digital Ocean Log in Networking Domains (Select your domain) More Manage Domain Domain.com Log in In card view, click manage on your domain In list view, click the gear icon DNS & Nameservers DNS Records Domains.com
WatchLog in (Select your domain) Manage (click gear icon) Click on DNS & Nameservers in left-hand menu DreamHost Log in Panel Domains Manage Domains DNS Dyn Log in Overview Manage Simple Editor Records Gandi Log in (Select your domain) Management Edit the zone GoDaddy
WatchLog in Manage My Domains (Select your domain) Manage DNS Google Domains
WatchLog in (Select your domain) Configure DNS Namecheap
WatchLog in Domain List (Select your domain) Manage Advanced DNS Netlify Log in (Select your domain) Setup Netlify DNS Network Solutions Log in Account Manager My Domain Names (Select your domain) Manage Change Where Domain Points Advanced DNS Shopify
WatchLog in Managed Domains (Select your domain) DNS Settings Squarespace Log in Home menu Settings Domains (Select your domain) Advanced settings Custom Records Vercel's Now Using "now" CLI now dns add [domain] '@' MX [record-value] [priority]Weebly Log in Domains page (Select your domain) DNS Wix Log in Domains page (Click icon) Select Manage DNS Records eNom Log in Domains My Domains Other Important: Don't see your registrar name listed here? Simply search on the Internet for "how to change DNS records on $REGISTRAR" (replacing $REGISTRAR with the name of your registrar – e.g. "how to change DNS records on GoDaddy" if you're using GoDaddy). - Using your registrar's DNS management page (the other tab you have opened), set the following "MX" records:
Important: Note that there should be NO other MX records set. Both records shown below MUST exist. Be sure there are no typos; and you have both mx1 and mx2 spelled correctly. If there were already MX records that existed, please delete them completely. The "TTL" value does not need to be 3600, it could be a lower or higher value if necessary.
Name/Host/Alias TTL Type Priority Answer/Value "@", ".", or blank 3600 MX 0 mx1.forwardemail.net"@", ".", or blank 3600 MX 0 mx2.forwardemail.net - Using your registrar's DNS management page (the other tab you have opened), set the following TXT record(s):
Important: If you are on a paid plan, then you must completely skip this step and go to step five! If you are not on a paid plan, then your forwarded addresses will be publicly searchable – go to My Account Domains and upgrade your domain to a paid plan if desired. If you would like to learn more about paid plans see our Pricing page. Otherwise you can continue to choose one or more combinations from Option A to Option F listed below.
Option A: If you are forwarding all emails from your domain, (e.g. "all@your-domain.your-domain.your-domain.your-domain.example.com", "hello@your-domain.your-domain.your-domain.your-domain.example.com", etc) to a specific address "user@gmail.com":Name/Host/Alias TTL Type Answer/Value "@", ".", or blank 3600 TXT forward-email=user@gmail.comTip: Make sure to replace the values above in the "Value" column with your own email address. The "TTL" value does not need to be 3600, it could be a lower or higher value if necessary. A lower time to live ("TTL") value will ensure any future changes made to your DNS records are propagated throughout the Internet quicker – think of this as how long it will be cached in-memory (in seconds). You can learn more about TTL on Wikipedia.
Option B: If you just need to forward a single email address (e.g.hello@your-domain.your-domain.your-domain.your-domain.example.comtouser@gmail.com; this will also forward "hello+test@your-domain.your-domain.your-domain.your-domain.example.com" to "user+test@gmail.com" automatically):Name/Host/Alias TTL Type Answer/Value "@", ".", or blank 3600 TXT forward-email=hello:user@gmail.com
Option C: If you are forwarding multiple emails, then you'll want to separate them with a comma:Name/Host/Alias TTL Type Answer/Value "@", ".", or blank 3600 TXT forward-email=hello:user@gmail.com,support:user@gmail.com
Option D: You can have an infinite amount of forwarding emails setup – just make sure to not wrap over 255 characters in a single-line and start each line with "forward-email=". An example is provided below:Name/Host/Alias TTL Type Answer/Value "@", ".", or blank 3600 TXT forward-email=hello:user@gmail.com,support:user@gmail.com"@", ".", or blank 3600 TXT forward-email=help:user@gmail.com,foo:user@gmail.com"@", ".", or blank 3600 TXT forward-email=orders:user@gmail.com,baz:user@gmail.com"@", ".", or blank 3600 TXT forward-email=info:user@gmail.com,beep:user@gmail.com"@", ".", or blank 3600 TXT forward-email=errors:user@gmail.com,boop:user@gmail.com
Option E: You can also specify a domain name in your TXT record to have global alias forwarding (e.g. "user@your-domain.your-domain.your-domain.your-domain.example.com" will get forwarded to "user@example.net"):Name/Host/Alias TTL Type Answer/Value "@", ".", or blank 3600 TXT forward-email=example.net
Option F: You can even use webhooks as a global or individual alias to forward emails to. See the example and full section on webhooks titled Do you support webhooks below.Name/Host/Alias TTL Type Answer/Value "@", ".", or blank 3600 TXT forward-email=alias:https://requestbin.com/r/en8pfhdgcculn
Option G: You can even use regular expressions ("regex") for matching aliases and for handling substitutions to forward emails to. See the examples and full section on regex titled Do you support regular expressions or regex below.Need advanced regex with substitution? See the examples and full section on regex titled Do you support regular expressions or regex below.Simple Example: If I want all emails that go to `linus@your-domain.your-domain.your-domain.your-domain.example.com` or `torvalds@your-domain.your-domain.your-domain.your-domain.example.com` to forward to `user@gmail.com`:Name/Host/Alias TTL Type Answer/Value "@", ".", or blank 3600 TXT forward-email=/^(linus|torvalds)$/:user@gmail.comImportant: Catch-all forwarding rules could also be described as "fall-through". This means that incoming emails which match at least one specific forwarding rule will be used instead of the catch-all. Specific rules include email addresses and regular expressions.
For example:
forward-email=hello:first@gmail.com,second@gmail.com
Emails sent tohello@your-domain.your-domain.your-domain.your-domain.example.comwill **not** be forwarded tosecond@gmail.com(catch-all) with this configuration, and instead only be delivered tofirst@gmail.com.
- Using your registrar's DNS management page (the other tab you have opened), additionally set the following TXT record:
Name/Host/Alias TTL Type Answer/Value "@", ".", or blank 3600 TXT v=spf1 a include:spf.forwardemail.net -allImportant: If you are using Gmail (e.g. Send Mail As) or G Suite, then you'll need to appendinclude:_spf.google.comto the value above, for example:
v=spf1 a include:spf.forwardemail.net include:_spf.google.com -allTip: If you already have a similar line with "v=spf1", then you'll need to appendinclude:spf.forwardemail.netright before any existing "include:host.com" records and before the "-all" in the same line, for example:
v=spf1 a include:spf.forwardemail.net include:host.com -all
Note that there is a difference between "-all" and "~all". The "-" indicates that the SPF check should FAIL if it does not match, and "~" indicates that the SPF check should SOFTFAIL. We recommend to use the "-all" approach to prevent domain forgery.
You may also need to include the SPF record for whichever host you are sending mail from (e.g. Outlook). - Verify your DNS records using our "Verify Records" tool available at My Account Domains Setup.
- Send a test email to confirm it works. Note that it might take some time for your DNS records to propagate.
Tip: If you are not receiving test emails, or receive a test email that says "Be careful with this message", then see the answers for Why am I not receiving my test emails and Why are my test emails sent to myself in Gmail showing as "suspicious" respectively.
- If you wish to "Send Mail As" from Gmail, then you will need to watch this video, or follow the steps under How to Send Mail As Using Gmail below.
Can I use multiple MX exchanges and servers for advanced forwarding
Yes, but you should only have one MX exchange listed in your DNS records.
Do not attempt to use "Priority" as a way to configure multiple MX exchanges.
Instead, you need to configure your existing MX exchange to forward mail for all non-matching aliases to our service's exchanges (mx1.forwardemail.net and/or mx2.forwardemail.net).
If you are using Google Workspace and you want to forward all non-matching aliases to our service, then see https://support.google.com/a/answer/6297084.
If you are using Microsoft 365 (Outlook) and you want to forward all non-matching aliases to our service, then see https://learn.microsoft.com/en-us/exchange/mail-flow-best-practices/use-connectors-to-configure-mail-flow/set-up-connectors-to-route-mail and https://learn.microsoft.com/en-us/exchange/mail-flow-best-practices/manage-mail-flow-for-multiple-locations.
How do I set up a vacation responder (out of office auto-responder)
Go to My Account Domains Aliases and either create or edit the alias you would like to configure a vacation autoresponder for.
You have the ability to configure a start date, end date, subject, and message, and enable or disable it at anytime:
- Plaintext subject and message are currently supported (we use
striptagspackage internally to remove any HTML). - Subject is limited to 100 characters.
- Message is limited to 1000 characters.
- Setup requires Outbound SMTP configuration (e.g. you will need to setup DKIM, DMARC, and Return-Path DNS records).
- Go to My Account Domains Settings Outbound SMTP Configuration and follow setup instructions.
- Vacation responder cannot be enabled on global vanity domain names (e.g. disposable addresses are not supported).
- Vacation responder cannot be enabled for aliases with wildcard/catch-all (
*) nor regular expressions.
Unlike mail systems such as postfix (e.g. that use the sieve vacation filter extension) – Forward Email automatically adds your DKIM signature, dummy-proofs connection issues when sending vacation responses (e.g. due to common SSL/TLS connection issues and legacy maintained servers), and even supports Open WKD and PGP encryption for vacation responses.
-
We only send once per allowlisted sender every 4 days (which is similar to Gmail's behavior).
-
Our Redis cache uses a fingerprint of
alias_idandsender, whereasalias_idis the alias MongoDB ID andsenderis either the From address (if allowlisted) or root domain in the From address (if not allowlisted). For simplicity the expiry of this fingerprint in cache is set to 4 days. -
Our approach of using the root domain parsed in the From address for non-allowlisted senders prevents abuse from relatively unknown senders (e.g. malicious actors) from flooding vacation responder messages.
-
-
We only send when the MAIL FROM and/or From is not blank and does not contain (case-insensitive) a postmaster username (the portion before the @ in an email).
-
We don't send if the original message had any of the following headers (case-insensitive):
- Header of
auto-submittedwith a value not equal tono. - Header of
x-auto-response-suppresswith a value ofdr,autoreply,auto-reply,auto_reply, orall - Header of
list-id,list-subscribe,list-unsubscribe,list-help,list-post,list-owner,list-archive,x-autoreply,x-autorespond, orx-auto-respond(regardless of value). - Header of
precedencewith a value ofbulk,autoreply,auto-reply,auto_reply, orlist.
- Header of
-
We don't send if the MAIL FROM or From email address ends with
+donotreply,-donotreply,+noreply, or-noreply. -
We don't send if the From email address username portion was
mdaemonand it had a case-insensitive header ofX-MDDSN-Message. -
We don't send if there was a case-insensitive
content-typeheader ofmultipart/report.
How do I set up SPF for Forward Email
Using your registrar's DNS management page, set the following TXT record:
| Name/Host/Alias | TTL | Type | Answer/Value |
|---|---|---|---|
| "@", ".", or blank | 3600 | TXT | v=spf1 a include:spf.forwardemail.net -all |
include:_spf.google.com to the value above, for example:
v=spf1 a include:spf.forwardemail.net include:_spf.google.com -all
include:spf.protection.outlook.com to your SPF TXT record, for example:
v=spf1 a include:spf.forwardemail.net include:spf.protection.outlook.com -all
include:spf.forwardemail.net right before any existing "include:host.com" records and before the "-all" in the same line, for example:
v=spf1 a include:spf.forwardemail.net include:host.com -all
Note that there is a difference between "-all" and "~all". The "-" indicates that the SPF check should FAIL if it does not match, and "~" indicates that the SPF check should SOFTFAIL. We recommend to use the "-all" approach to prevent domain forgery.
You may also need to include the SPF record for whichever host you are sending mail from (e.g. Outlook).
How do I set up DKIM for Forward Email
Go to My Account Domains Settings Outbound SMTP Configuration and follow setup instructions.
How do I set up DMARC for Forward Email
Go to My Account Domains Settings Outbound SMTP Configuration and follow setup instructions.
How do I view DMARC Reports
Forward Email provides a comprehensive DMARC Reports dashboard that allows you to monitor your email authentication performance across all your domains from a single interface.
What are DMARC Reports?
DMARC (Domain-based Message Authentication, Reporting, and Conformance) reports are XML files sent by receiving mail servers that tell you how your emails are being authenticated. These reports help you understand:
- How many emails are being sent from your domain
- Whether those emails are passing SPF and DKIM authentication
- What actions receiving servers are taking (accept, quarantine, or reject)
- Which IP addresses are sending email on behalf of your domain
How to Access DMARC Reports
Go to My Account DMARC Reports to view your dashboard. You can also access domain-specific reports from My Account Domains by clicking the "DMARC" button next to any domain.
Dashboard Features
The DMARC Reports dashboard provides:
- Summary Metrics: Total reports received, total messages analyzed, SPF alignment rate, DKIM alignment rate, and overall pass rate
- Messages Over Time Chart: Visual trend of email volume and authentication rates over the past 30 days
- Alignment Summary: Donut chart showing SPF vs DKIM alignment distribution
- Message Disposition: Stacked bar chart showing how receiving servers handled your emails (accepted, quarantined, or rejected)
- Recent Reports Table: Detailed list of individual DMARC reports with filtering and pagination
- Domain Filtering: Filter reports by specific domain when managing multiple domains
Why This Matters
For organizations managing multiple domains (like enterprises, non-profits, or agencies), DMARC reports are essential for:
- Identifying unauthorized senders: Detect if someone is spoofing your domain
- Improving deliverability: Ensure your legitimate emails pass authentication
- Monitoring email infrastructure: Track which services and IPs are sending on your behalf
- Compliance: Maintain visibility into email authentication for security audits
Unlike other services that require separate DMARC monitoring tools, Forward Email includes DMARC report processing and visualization as part of your account at no additional cost.
Requirements
- DMARC Reports are available for paid plans only
- Your domain must have DMARC configured (see How do I set up DMARC for Forward Email)
- Reports are automatically collected when receiving mail servers send them to your configured DMARC reporting address
Weekly Email Reports
Paid plan users automatically receive weekly DMARC report summaries via email. These emails include:
- Summary statistics for all your domains
- SPF and DKIM alignment rates
- Message disposition breakdown (accepted, quarantined, rejected)
- Top reporting organizations (Google, Microsoft, Yahoo, etc.)
- IP addresses with alignment issues that may need attention
- Direct links to your DMARC Reports dashboard
Weekly reports are sent automatically and cannot be disabled separately from other email notifications.
How do I connect and configure my contacts
To configure your contacts, use the CardDAV URL of: https://carddav.forwardemail.net (or simply carddav.forwardemail.net if your client allows it)
How do I connect and configure my calendars
To configure your calendar, use the CalDAV URL of: https://caldav.forwardemail.net (or simply caldav.forwardemail.net if your client allows it)
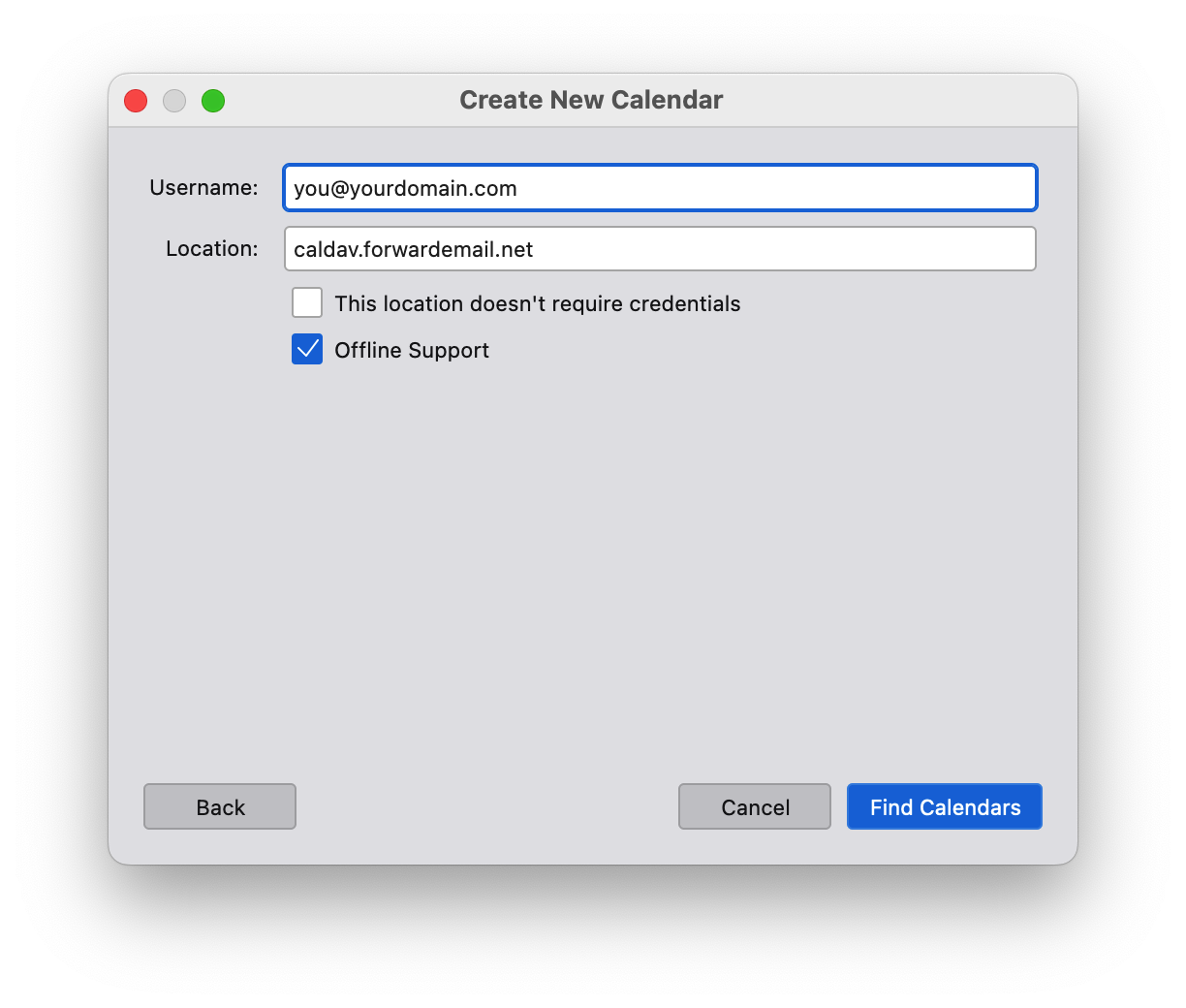
How do I add more calendars and manage existing calendars
If you'd like to add additional calendars, then just add a new calendar URL of: https://caldav.forwardemail.net/dav/principals/calendar-name (be sure to replace calendar-name with your desired calendar name)
You can change a calendar's name and color after creation – just use your preferred calendar application (e.g. Apple Mail or Thunderbird).
How do I connect and configure tasks and reminders
To configure tasks and reminders, use the same CalDAV URL as calendars: https://caldav.forwardemail.net (or simply caldav.forwardemail.net if your client allows it)
Tasks and reminders will automatically be separated from calendar events into their own "Reminders" or "Tasks" calendar collection.
Setup instructions by platform:
macOS/iOS:
- Add a new CalDAV account in System Preferences > Internet Accounts (or Settings > Accounts on iOS)
- Use
caldav.forwardemail.netas the server - Enter your Forward Email alias and generated password
- After setup, you'll see both "Calendar" and "Reminders" collections
- Use the Reminders app to create and manage tasks
Android with Tasks.org:
- Install Tasks.org from Google Play Store or F-Droid
- Go to Settings > Synchronization > Add Account > CalDAV
- Enter server:
https://caldav.forwardemail.net - Enter your Forward Email alias and generated password
- Tasks.org will automatically discover your task calendars
Thunderbird:
- Install the Lightning add-on if not already installed
- Create a new calendar with type "CalDAV"
- Use URL:
https://caldav.forwardemail.net - Enter your Forward Email credentials
- Both events and tasks will be available in the calendar interface
Why can't I create tasks in macOS Reminders
If you're having trouble creating tasks in macOS Reminders, try these troubleshooting steps:
-
Check account setup: Ensure your CalDAV account is properly configured with
caldav.forwardemail.net -
Verify separate calendars: You should see both "Calendar" and "Reminders" in your account. If you only see "Calendar", the task support may not be fully activated yet.
-
Refresh account: Try removing and re-adding your CalDAV account in System Preferences > Internet Accounts
-
Check server connectivity: Test that you can access
https://caldav.forwardemail.netin your browser -
Verify credentials: Ensure you're using the correct alias email and generated password (not your account password)
-
Force sync: In Reminders app, try creating a task and then manually refreshing the sync
Common issues:
- "Reminders calendar not found": The server may need a moment to create the Reminders collection on first access
- Tasks not syncing: Check that both devices are using the same CalDAV account credentials
- Mixed content: Ensure tasks are being created in the "Reminders" calendar, not the general "Calendar"
How do I set up Tasks.org on Android
Tasks.org is a popular open-source task manager that works excellently with Forward Email's CalDAV task support.
Installation and Setup:
-
Install Tasks.org:
- From Google Play Store: Tasks.org
- From F-Droid: Tasks.org on F-Droid
-
Configure CalDAV sync:
- Open Tasks.org
- Go to ☰ Menu > Settings > Synchronization
- Tap "Add Account"
- Select "CalDAV"
-
Enter Forward Email settings:
- Server URL:
https://caldav.forwardemail.net - Username: Your Forward Email alias (e.g.,
you@yourdomain.com) - Password: Your alias-specific generated password
- Tap "Add Account"
- Server URL:
-
Account discovery:
- Tasks.org will automatically discover your task calendars
- You should see your "Reminders" collection appear
- Tap "Subscribe" to enable sync for the task calendar
-
Test sync:
- Create a test task in Tasks.org
- Check that it appears in other CalDAV clients (like macOS Reminders)
- Verify changes sync both ways
Features available:
- ✅ Task creation and editing
- ✅ Due dates and reminders
- ✅ Task completion and status
- ✅ Priority levels
- ✅ Subtasks and task hierarchy
- ✅ Tags and categories
- ✅ Two-way sync with other CalDAV clients
Troubleshooting:
- If no task calendars appear, try manually refreshing in Tasks.org settings
- Ensure you have at least one task created on the server (you can create one in macOS Reminders first)
- Check network connectivity to
caldav.forwardemail.net
How do I set up SRS for Forward Email
We automatically configure Sender Rewriting Scheme ("SRS") – you do not need to do this yourself.
How do I set up MTA-STS for Forward Email
Please refer to our section on MTA-STS for more insight.
How do I add a profile picture to my email address
If you're using Gmail, then follow these steps below:
- Go to https://google.com and sign out of all email accounts
- Click "Sign In" and on the drop-down click on "other account"
- Select "Use another account"
- Select "Create account"
- Select "Use my current email address instead"
- Enter your custom domain name email address
- Retrieve the verification email sent to your email address
- Enter the verification code from this email
- Complete profile information for your new Google account
- Agree to all Privacy and Terms of Use policies
- Go to https://google.com and in the top right corner, click on your profile icon, and click on the "change" button
- Upload a new photo or avatar for your account
- Changes will take approximately 1-2 hours to propagate, but sometimes may be very quick.
- Send a test email and the profile photo should appear.
Advanced Features
Do you support newsletters or mailing lists for marketing related email
Yes, you can read more at https://forwardemail.net/guides/newsletter-with-listmonk.
Please note that in order to maintain IP reputation and ensure deliverability, Forward Email has a manual review process on a per-domain basis for newsletter approval. Email support@forwardemail.net or open a help request for approval. This typically takes less than 24 hours, with most requests being honored within 1-2 hours. In the near future we aim to make this process instant with additional spam controls and alerting. This process ensures that your emails reach the inbox and your messages don't get marked as spam.
Do you support sending email with API
Yes, as of May 2023 we support sending email with API as an add-on for all paid users.
Please view our section on Emails in our API documentation for options, examples, and more insight.
In order to send outbound email with our API, you must use your API token available under My Security.
Do you support receiving email with IMAP
Yes, as of October 16, 2023 we support receiving email over IMAP as an add-on for all paid users. Please read our deep-dive article on how our encrypted SQLite mailbox storage feature works.
-
Create a new alias for your domain under My Account Domains Aliases (e.g.
hello@your-domain.your-domain.your-domain.your-domain.example.com) -
Click on Generate Password next to the newly created alias. Copy to your clipboard and securely store the generated password shown on the screen.
-
Using your preferred email application, add or configure an account with your newly created alias (e.g.
hello@your-domain.your-domain.your-domain.your-domain.example.com)Tip: We recommend using Thunderbird, Thunderbird Mobile, Apple Mail, or an open-source and privacy-focused alternative. -
When prompted for IMAP server name, enter
imap.forwardemail.net -
When prompted for IMAP server port, enter
993(SSL/TLS) – see alternate IMAP ports if necessaryTip: If you are using Thunderbird, then ensure "Connection security" is set to "SSL/TLS" and Authentication method is set to "Normal password". -
When prompted for IMAP server password, paste the password from Generate Password in step 2 above
-
Save your settings – if you are having issues, then please contact us
Do you support POP3
Yes, as of December 4, 2023 we support POP3 as an add-on for all paid users. Please read our deep-dive article on how our encrypted SQLite mailbox storage feature works.
-
Create a new alias for your domain under My Account Domains Aliases (e.g.
hello@your-domain.your-domain.your-domain.your-domain.example.com) -
Click on Generate Password next to the newly created alias. Copy to your clipboard and securely store the generated password shown on the screen.
-
Using your preferred email application, add or configure an account with your newly created alias (e.g.
hello@your-domain.your-domain.your-domain.your-domain.example.com)Tip: We recommend using Thunderbird, Thunderbird Mobile, Apple Mail, or an open-source and privacy-focused alternative. -
When prompted for POP3 server name, enter
pop3.forwardemail.net -
When prompted for POP3 server port, enter
995(SSL/TLS) – see alternate POP3 ports if necessaryTip: If you are using Thunderbird, then ensure "Connection security" is set to "SSL/TLS" and Authentication method is set to "Normal password". -
When prompted for POP3 server password, paste the password from Generate Password in step 2 above
-
Save your settings – if you are having issues, then please contact us
Do you support calendars (CalDAV)
Yes, as of February 5, 2024 we have added this feature. Our server is caldav.forwardemail.net and is also monitored on our status page.
It supports both IPv4 and IPv6 and is available over port 443 (HTTPS).
| Login | Example | Description |
|---|---|---|
| Username | user@your-domain.your-domain.your-domain.your-domain.example.com |
Email address of an alias that exists for the domain at My Account Domains. |
| Password | ************************ |
Alias-specific generated password. |
In order to use calendar support, the user must be the email address of an alias that exists for the domain at My Account Domains – and the password must be an alias-specific generated password.
Do you support tasks and reminders (CalDAV VTODO)
Yes, as of October 14, 2025 we have added CalDAV VTODO support for tasks and reminders. This uses the same server as our calendar support: caldav.forwardemail.net.
Our CalDAV server supports both calendar events (VEVENT) and tasks (VTODO) components using unified calendars. This means each calendar can contain both events and tasks, providing maximum flexibility and compatibility across all CalDAV clients.
How calendars and lists work:
- Each calendar supports both events and tasks - You can add events, tasks, or both to any calendar
- Apple Reminders lists - Each list you create in Apple Reminders becomes a separate calendar on the server
- Multiple calendars - You can create as many calendars as you need, each with its own name, color, and organization
- Cross-client sync - Tasks and events sync seamlessly between all compatible clients
Supported task clients:
- macOS Reminders - Full native support for task creation, editing, completion, and sync
- iOS Reminders - Full native support across all iOS devices
- Tasks.org (Android) - Popular open-source task manager with CalDAV sync
- Thunderbird - Task and calendar support in desktop email client
- Any CalDAV-compatible task manager - Standard VTODO component support
Task features supported:
- Task creation, editing, and deletion
- Due dates and start dates
- Task completion status (NEEDS-ACTION, IN-PROCESS, COMPLETED, CANCELLED)
- Task priority levels
- Recurring tasks
- Task descriptions and notes
- Multi-device synchronization
- Subtasks with RELATED-TO property
- Task reminders with VALARM
The login credentials are the same as for calendar support:
| Login | Example | Description |
|---|---|---|
| Username | user@your-domain.your-domain.your-domain.your-domain.example.com |
Email address of an alias that exists for the domain at My Account Domains. |
| Password | ************************ |
Alias-specific generated password. |
Important notes:
- Each Reminders list is a separate calendar - When you create a new list in Apple Reminders, it creates a new calendar on the CalDAV server
- Thunderbird users - You'll need to manually subscribe to each calendar/list you want to sync, or use the calendar home URL:
https://caldav.forwardemail.net/dav/your-email@domain.com/ - Apple users - Calendar discovery happens automatically, so all your calendars and lists will appear in Calendar.app and Reminders.app
- Unified calendars - All calendars support both events and tasks, giving you flexibility in how you organize your data
Do you support contacts (CardDAV)
Yes, as of June 12, 2025 we have added this feature. Our server is carddav.forwardemail.net and is also monitored on our status page.
It supports both IPv4 and IPv6 and is available over port 443 (HTTPS).
| Login | Example | Description |
|---|---|---|
| Username | user@your-domain.your-domain.your-domain.your-domain.example.com |
Email address of an alias that exists for the domain at My Account Domains. |
| Password | ************************ |
Alias-specific generated password. |
In order to use contacts support, the user must be the email address of an alias that exists for the domain at My Account Domains – and the password must be an alias-specific generated password.
Do you support sending email with SMTP
Yes, as of May 2023 we support sending email with SMTP as an add-on for all paid users.
-
Go to My Account Domains Settings Outbound SMTP Configuration and follow setup instructions
-
Create a new alias for your domain under My Account Domains Aliases (e.g.
hello@your-domain.your-domain.your-domain.your-domain.example.com) -
Click on Generate Password next to the newly created alias. Copy to your clipboard and securely store the generated password shown on the screen.
-
Using your preferred email application, add or configure an account with your newly created alias (e.g.
hello@your-domain.your-domain.your-domain.your-domain.example.com)Tip: We recommend using Thunderbird, Thunderbird Mobile, Apple Mail, or an open-source and privacy-focused alternative. -
When prompted for SMTP server name, enter
smtp.forwardemail.net -
When prompted for SMTP server port, enter
465(SSL/TLS) – see alternate SMTP ports if necessaryTip: If you are using Thunderbird, then ensure "Connection security" is set to "SSL/TLS" and Authentication method is set to "Normal password". -
When prompted for SMTP server password, paste the password from Generate Password in step 3 above
-
Save your settings and send your first test email – if you are having issues, then please contact us
Do you support OpenPGP/MIME, end-to-end encryption ("E2EE"), and Web Key Directory ("WKD")
Yes, we support OpenPGP, end-to-end encryption ("E2EE"), and the discovery of public keys using Web Key Directory ("WKD"). You can configure OpenPGP using keys.openpgp.org or self-host your own keys (refer to this gist for WKD server setup).
- WKD lookups are cached for 1 hour to ensure timely email delivery → therefore if you add, change, or remove your WKD key, then please email us at
support@forwardemail.netwith your email address in order for us to manually purge the cache. - We support PGP encryption for messages that are forwarded via WKD lookup or using an uploaded PGP key on our interface.
- Uploaded keys take prevalance as long as the PGP checkbox is enabled/checked.
- Messages sent to webhooks are not currently encrypted with PGP.
- If you have multiple aliases that match for a given forwarding address (e.g. regex/wildcard/exact combo) and if more than one of these contains an uploaded PGP key and has PGP checked → then we will send you an error alert email and will not encrypt the message with your uploaded PGP key. This is very rare and usually only applies to advanced users with complex alias rules.
- PGP encryption will not be applied to email forwarding through our MX servers if the sender had a DMARC policy of reject. If you require PGP encryption on all mail then we suggest to use our IMAP service and configure your PGP key for your alias for inbound mail.
You can validate your Web Key Directory setup at https://wkd.chimbosonic.com/ (open-source) or https://www.webkeydirectory.com/ (proprietary).
-
Download and install your email client's recommended plugin below:
Email Client Platform Recommended Plugin Notes Thunderbird Desktop Configure OpenPGP in Thunderbird Thunderbird has built-in support for OpenPGP. Gmail Browser Mailvelope or FlowCrypt (proprietary license) Gmail does not support OpenPGP, however you can download the open-source plugin Mailvelope or FlowCrypt. Apple Mail macOS Free-GPGMail Apple Mail does not support OpenPGP, however you can download the open-source plugin Free-GPGMail. Apple Mail iOS PGPro or FlowCrypt (proprietary license) Apple Mail does not support OpenPGP, however you can download the open-source plugin PGPro or FlowCrypt. Outlook Windows gpg4win Outlook's desktop mail client does not support OpenPGP, however you can download the open-source plugin gpg4win. Outlook Browser Mailvelope or FlowCrypt (proprietary license) Outlook's web-based mail client does not support OpenPGP, however you can download the open-source plugin Mailvelope or FlowCrypt. Android Mobile OpenKeychain or FlowCrypt Android mail clients such as Thunderbird Mobile and FairEmail both support the open-source plugin OpenKeychain. You could alternatively use the open-source (proprietary licensing) plugin FlowCrypt. Google Chrome Browser Mailvelope or FlowCrypt (proprietary license) You can download the open-source browser extension Mailvelope or FlowCrypt. Mozilla Firefox Browser Mailvelope or FlowCrypt (proprietary license) You can download the open-source browser extension Mailvelope or FlowCrypt. Microsoft Edge Browser Mailvelope You can download the open-source browser extension Mailvelope. Brave Browser Mailvelope or FlowCrypt (proprietary license) You can download the open-source browser extension Mailvelope or FlowCrypt. Balsa Desktop Configure OpenPGP in Balsa Balsa has built-in support for OpenPGP. KMail Desktop Configure OpenPGP in KMail KMail has built-in support for OpenPGP. GNOME Evolution Desktop Configure OpenPGP in Evolution GNOME Evolution has built-in support for OpenPGP. Terminal Desktop Configure gpg in Terminal You can use the open-source gpg command line tool to generate a new key from command line. -
Open the plugin, create your public key, and configure your email client to use it.
-
Upload your public key at https://keys.openpgp.org/upload.
Tip: You can visit https://keys.openpgp.org/manage to manage your key in the future.Optional Add-on: If you are using our encrypted storage (IMAP/POP3) service and want all email stored in your (already encrypted) SQLite database to be encrypted with your public key, then go to My Account Domains Aliases (e.g.hello@your-domain.your-domain.your-domain.your-domain.example.com) Edit OpenPGP and upload your public key. -
Add a new
CNAMErecord to your domain name (e.g.your-domain.your-domain.your-domain.your-domain.example.com):Name/Host/Alias TTL Type Answer/Value openpgpkey3600 CNAME wkd.keys.openpgp.orgTip: If your alias is using our vanity/disposable domains (e.g.hideaddress.net), then you can skip this step.
Do you support S/MIME encryption
Yes, we support S/MIME (Secure/Multipurpose Internet Mail Extensions) encryption as defined in RFC 8551. S/MIME provides end-to-end encryption using X.509 certificates, which is widely supported by enterprise email clients.
We support both RSA and ECC (Elliptic Curve Cryptography) certificates:
- RSA certificates: 2048-bit minimum, 4096-bit recommended
- ECC certificates: P-256, P-384, and P-521 NIST curves
To configure S/MIME encryption for your alias:
-
Obtain an S/MIME certificate from a trusted Certificate Authority (CA) or generate a self-signed certificate for testing.
Tip: Free S/MIME certificates are available from providers like Actalis or Actalis Free S/MIME. -
Export your certificate in PEM format (the public certificate only, not the private key).
-
Go to My Account Domains Aliases (e.g.
hello@your-domain.your-domain.your-domain.your-domain.example.com) Edit S/MIME and upload your public certificate. -
Once configured, all incoming emails to your alias will be encrypted using your S/MIME certificate before being stored or forwarded.
Note: S/MIME encryption is applied to incoming messages that are not already encrypted. If a message is already encrypted with OpenPGP or S/MIME, it will not be re-encrypted.Important: S/MIME encryption will not be applied to email forwarding through our MX servers if the sender had a DMARC policy of reject. If you require S/MIME encryption on all mail then we suggest to use our IMAP service and configure your S/MIME certificate for your alias for inbound mail.
The following email clients have built-in S/MIME support:
| Email Client | Platform | Notes |
|---|---|---|
| Apple Mail | macOS | Built-in S/MIME support. Go to Mail > Preferences > Accounts > your account > Trust to configure certificates. |
| Apple Mail | iOS | Built-in S/MIME support. Go to Settings > Mail > Accounts > your account > Advanced > S/MIME to configure. |
| Microsoft Outlook | Windows | Built-in S/MIME support. Go to File > Options > Trust Center > Trust Center Settings > Email Security to configure. |
| Microsoft Outlook | macOS | Built-in S/MIME support. Go to Tools > Accounts > Advanced > Security to configure. |
| Thunderbird | Desktop | Built-in S/MIME support. Go to Account Settings > End-To-End Encryption > S/MIME to configure. |
| GNOME Evolution | Desktop | Built-in S/MIME support. Go to Edit > Preferences > Mail Accounts > your account > Security to configure. |
| KMail | Desktop | Built-in S/MIME support. Go to Settings > Configure KMail > Identities > your identity > Cryptography to configure. |
Do you support Sieve email filtering
Yes! We support Sieve email filtering as defined in RFC 5228. Sieve is a powerful, standardized scripting language for server-side email filtering that allows you to automatically organize, filter, and respond to incoming messages.
Supported Sieve Extensions
We support a comprehensive set of Sieve extensions:
| Extension | RFC | Description |
|---|---|---|
fileinto |
RFC 5228 | File messages into specific folders |
reject / ereject |
RFC 5429 | Reject messages with an error |
vacation |
RFC 5230 | Automatic vacation/out-of-office replies |
vacation-seconds |
RFC 6131 | Fine-grained vacation response intervals |
imap4flags |
RFC 5232 | Set IMAP flags (\Seen, \Flagged, etc.) |
envelope |
RFC 5228 | Test envelope sender/recipient |
body |
RFC 5173 | Test message body content |
variables |
RFC 5229 | Store and use variables in scripts |
relational |
RFC 5231 | Relational comparisons (greater than, less than) |
comparator-i;ascii-numeric |
RFC 4790 | Numeric comparisons |
copy |
RFC 3894 | Copy messages while redirecting |
editheader |
RFC 5293 | Add or delete message headers |
date |
RFC 5260 | Test date/time values |
index |
RFC 5260 | Access specific header occurrences |
regex |
draft-ietf-sieve-regex | Regular expression matching |
enotify |
RFC 5435 | Send notifications (e.g., mailto:) |
environment |
RFC 5183 | Access environment information |
mailbox |
RFC 5490 | Test mailbox existence, create mailboxes |
special-use |
RFC 8579 | File into special-use mailboxes (\Junk, \Trash) |
duplicate |
RFC 7352 | Detect duplicate messages |
ihave |
RFC 5463 | Test for extension availability |
subaddress |
RFC 5233 | Access user+detail address parts |
Extensions Not Supported
The following extensions are not currently supported:
| Extension | Reason |
|---|---|
include |
Security risk (script injection) and requires global script storage |
mboxmetadata / servermetadata |
Requires IMAP METADATA extension support |
foreverypart / mime / extracttext / replace / enclose |
Complex MIME tree manipulation not yet implemented |
Example Sieve Scripts
File newsletters into a folder:
require ["fileinto"];
if header :contains "List-Id" "newsletter" {
fileinto "Newsletters";
}
Auto-reply when on vacation:
require ["vacation"];
vacation :days 7 :subject "Out of Office"
"I am currently out of the office and will respond when I return.";
Mark messages from important senders:
require ["imap4flags"];
if address :is "from" "boss@your-domain.your-domain.your-domain.your-domain.example.com" {
setflag "\\Flagged";
}
Reject spam with specific subjects:
require ["reject"];
if header :contains "subject" ["lottery", "winner", "urgent transfer"] {
reject "Message rejected due to spam content.";
}
Managing Sieve Scripts
You can manage your Sieve scripts in several ways:
-
Web Interface: Go to My Account Domains Aliases Sieve Scripts to create and manage scripts.
-
ManageSieve Protocol: Connect using any ManageSieve-compatible client (like Thunderbird's Sieve add-on or sieve-connect) to
imap.forwardemail.net. Use port2190with STARTTLS (recommended for most clients) or port4190with implicit TLS. -
API: Use our REST API to programmatically manage scripts.
Do you support MTA-STS
Yes, as of March 2, 2023 we support MTA-STS. You can use this template if you wish to enable it on your domain.
Our configuration can be found publicly on GitHub at https://github.com/forwardemail/mta-sts.forwardemail.net.
Do you support passkeys and WebAuthn
Yes! As of December 13, 2023 we have added support for passkeys due to high demand.
Passkeys allow you to securely log in without requiring a password and two-factor authentication.
You can validate your identity with touch, facial recognition, device-based password, or PIN.
We allow you to manage up to 30 passkeys at once, so that you can log in with all of your devices with ease.
Learn more about passkeys at the following links:
- Sign-in to your applications and websites with passkeys (Google)
- Use passkeys to sign in to apps and websites on iPhone (Apple)
- Wikipedia article on Passkeys
Do you support email best practices
Yes. We have built-in support for SPF, DKIM, DMARC, ARC, and SRS across all plans. We have also worked extensively with the original authors of these specifications and other email experts to ensure perfection and high deliverability.
Do you support bounce webhooks
Yes, as of August 14, 2024 we have added this feature. You can now go to My Account → Domains → Settings → Bounce Webhook URL and configure an http:// or https:// URL that we will send a POST request to whenever outbound SMTP emails bounce.
This is useful for you to manage and monitor your outbound SMTP – and can be used to maintain subscribers, opt-out, and detect whenever bounces occur.
Bounce webhook payloads are sent as a JSON with these properties:
email_id(String) - email ID that corresponds to an email in My Account → Emails (outbound SMTP)list_id(String) - theList-IDheader (case-insensitive) value, if any, from the original outbound emaillist_unsubscribe(String) - theList-Unsubscribeheader (case-insensitive) value, if any, from the original outbound emailfeedback_id(String) - theFeedback-IDheader (case-insensitive) value, if any, from the original outbound emailrecipient(String) - the email address of the recipient that bounced or erroredmessage(String) - a detailed error message for the bounceresponse(String) - the SMTP response messageresponse_code(Number) - the parsed SMTP response codetruth_source(String) - if the response code was from a trusted source, this value will be populated with the root domain name (e.g.google.comoryahoo.com)bounce(Object) - an object containing the following properties that detail the bounce and rejection statusaction(String) - bounce action (e.g."reject")message(String) - bounce reason (e.g."Message Sender Blocked By Receiving Server")category(String) - bounce category (e.g."block")code(Number) - bounce status code (e.g.554)status(String) - bounce code from response message (e.g.5.7.1)line(Number) - parsed line number, if any, from Zone-MTA bounce parse list (e.g.526)
headers(Object) - key value pair of headers for the outbound emailbounced_at(String) - ISO 8601 formatted Date for when the bounce error occurred
For example:
{
"email_id": "66bcce793ef7b2a0928e14ba",
"recipient": "example@gmail.com",
"message": "The email account that you tried to reach is over quota.",
"response": "552 5.2.2 The email account that you tried to reach is over quota.",
"response_code": 552,
"truth_source": "google.com",
"bounce": {
"action": "reject",
"message": "Gmail Mailbox is full",
"category": "capacity",
"code": 552,
"status": "5.2.2",
"line": 300
},
"headers": {},
"bounced_at": "2024-08-24T01:50:02.828Z"
}
Here are a few additional notes regarding bounce webhooks:
- If the webhook payload contains a
list_id,list_unsubscribe, orfeedback_idvalue, then you should take appropriate action to remove therecipientfrom the list if necessary.- If the
bounce.categoryvalue was one"block","recipient","spam", or"virus", then you should definitely remove the user from the list.
- If the
- If you need to verify webhook payloads (to ensure they're actually coming from our server), then you can resolve the remote client IP address client hostname using a reverse lookup – it should be
smtp.forwardemail.net.- You can also check the IP against our published IP addresses.
- Go to My Account → Domains → Settings → Webhook Signature Payload Verification Key to obtain your webhook key.
- You can rotate this key at anytime for security reasons.
- Calculate and compare the
X-Webhook-Signaturevalue from our webhook request with the computed body value using this key. An example of how to do this is available at this Stack Overflow post.
- See the discussion at https://github.com/forwardemail/free-email-forwarding/issues/235 for more insight.
- We will wait for up to
5seconds for your webhook endpoint to respond with a200status code, and we will retry up to1time. - If we detect that your bounce webhook URL has an error while we try to send a request to it, then we will send you a courtesy email once a week.
Do you support webhooks
Yes, as of May 15, 2020 we have added this feature. You can simply add webhook(s) exactly like you would with any recipient! Please ensure that you have the "http" or "https" protocol prefixed in the webhook's URL.
If you are on the free plan, then simply add a new DNS TXT record as shown below:
For example, if I want all emails that go to alias@your-domain.your-domain.your-domain.your-domain.example.com to forward to a new request bin test endpoint:
| Name/Host/Alias | TTL | Type | Answer/Value |
|---|---|---|---|
| "@", ".", or blank | 3600 | TXT | forward-email=alias:https://requestbin.com/r/en8pfhdgcculn |
Or perhaps you want all emails that go to your-domain.your-domain.your-domain.your-domain.example.com to forward to this endpoint:
| Name/Host/Alias | TTL | Type | Answer/Value |
|---|---|---|---|
| "@", ".", or blank | 3600 | TXT | forward-email=https://requestbin.com/r/en8pfhdgcculn |
Here are additional notes regarding webhooks:
-
If you need to verify webhook payloads (to ensure they're actually coming from our server), then you can resolve the remote client IP address client hostname using a reverse lookup – it should be either
mx1.forwardemail.netormx2.forwardemail.net.- You can also check the IP against our published IP addresses.
- If you're on a paid plan, then go to My Account → Domains → Settings → Webhook Signature Payload Verification Key to obtain your webhook key.
- You can rotate this key at anytime for security reasons.
- Calculate and compare the
X-Webhook-Signaturevalue from our webhook request with the computed body value using this key. An example of how to do this is available at this Stack Overflow post.
- See the discussion at https://github.com/forwardemail/free-email-forwarding/issues/235 for more insight.
-
If a webhook does not respond with a
200status code, then we will store its response in the error log created – which is useful for debugging. -
Webhook HTTP requests will retry up to 3 times every SMTP connection attempt, with a 60 second max timeout per endpoint POST request. Note that this does not mean that it only retries 3 times, it will actually retry continously over time by sending a SMTP code of 421 (which indicates to the sender retry later) after the 3rd failed HTTP POST request attempt. This means the email will retry continuously for days until a 200 status code is achieved.
-
We will retry automatically based off the default status and error codes used in superagent's retry method (we are maintainers).
-
We group together webhook HTTP requests to the same endpoint in one request instead of multiple) in order to save resources and speed up response time. For example, if you send an email to webhook1@your-domain.your-domain.your-domain.your-domain.example.com, webhook2@your-domain.your-domain.your-domain.your-domain.example.com, and webhook3@your-domain.your-domain.your-domain.your-domain.example.com, and all of these are configured to hit the same exact endpoint URL, then only one request will be made. We group together by exact endpoint matching with strict equality.
-
Note that we use the mailparser library's "simpleParser" method to parse the message into a JSON friendly object.
-
Raw email value as a String is given as the property "raw".
-
Authentication results are given as properties "dkim", "spf", "arc", "dmarc", and "bimi".
-
The parsed email headers is given as the property "headers" – but also note you can use "headerLines" for easier iteration and parsing.
-
The grouped recipients for this webhook are grouped together and given as the property "recipients".
-
The SMTP session information is given as the property "session". This contains information about the sender of the message, arrival time of the message, HELO, and client hostname. The client hostname value as
session.clientHostnameis either the FQDN (from a reverse PTR lookup) or it issession.remoteAddresswrapped in brackets (e.g."[127.0.0.1]"). -
If you need a quick way to get the value of
X-Original-To, then you can use the value ofsession.recipient(see example below). The headerX-Original-Tois a header we add to messages for debugging with the original recipient (before masked forwarding) for the message. -
If you need to remove
attachmentsand/orrawproperties from the payload body, simply add?attachments=false,?raw=false, or?attachments=false&raw=falseto your webhook endpoint as a querystring parameter (e.g.https://your-domain.your-domain.your-domain.your-domain.example.com/webhook?attachments=false&raw=false). -
If there are attachments, they will be appended to the
attachmentsArray with Buffer values. You can parse them back into content using an approach with JavaScript such as:const data = [ 104, 101, 108, 108, 111, 32, 119, 111, 114, 108, 100, 33 ]; // // outputs "hello world!" to the console // (this is the content from the filename "text1.txt" in the example JSON request payload above) // console.log(Buffer.from(data).toString());
{
"attachments": [
{
"type": "attachment",
"content": {
"type": "Buffer",
"data": [
104,
101,
108,
108,
111,
32,
119,
111,
114,
108,
100,
33
]
},
"contentType": "text/plain",
"partId": "2",
"release": null,
"contentDisposition": "attachment",
"filename": "text1.txt",
"headers": {},
"checksum": "fc3ff98e8c6a0d3087d515c0473f8677",
"size": 12
}
],
"headers": "ARC-Seal: i=1; a=rsa-sha256; t=1653506802; cv=none; d=forwardemail.net;\r\n s=default;\r\n b=R6QJ0tGwwjg2VPxiAlVIKxsg3jEPtRGKPTIOdZNWuhWrbssttFdOYzRRqvacDyN5SLoyDhVye\r\n DUA/64IxANXdHVFlpR258Yp7WxLDv2gtJD5vNSKYmUJZOWk1TynmlqTYrp0Vuqg2xIUjIlPBWAJ\r\n PPNx4JvOLjJuWYynU2qIWz0=\r\nARC-Message-Signature: i=1; a=rsa-sha256; c=relaxed/relaxed;\r\n d=forwardemail.net; h=MIME-Version: Date: Message-ID: From: Content-Type;\r\n q=dns/txt; s=default; t=1653506802;\r\n bh=cEYDoyTy+Ub29XZt/zXR+sprfUE6BW0y5cHfah01PT4=;\r\n b=F/t56AAXr2Kv3G6VsbdT5OKDVJf2ulhwLiTM18Ra4tDPUKPSGSLKrWvxiXEg5NMWwdWnsOYrL\r\n r3YSm4uMxVMhHZbHm/sUu4QZq5/18hQsAkCv6fI9ifTjDwBrN5zpLOhPoZFFo+TyvHxiII3Xv3L\r\n UEzmUIIaJRX6tboQ160tino=\r\nARC-Authentication-Results: i=1; mx1.forwardemail.net;\r\n dkim=none (message not signed);\r\n spf=none (mx1.forwardemail.net: example.net does not designate permitted sender hosts) smtp.mailfrom=test@example.net smtp.helo=user.oem.local;\r\n dmarc=none header.from=your-domain.your-domain.your-domain.your-domain.example.com;\r\n bimi=skipped (DMARC not enabled)\r\nReceived-SPF: none (mx1.forwardemail.net: example.net does not designate permitted sender hosts) client-ip=127.0.0.1;\r\nAuthentication-Results: mx1.forwardemail.net;\r\n dkim=none (message not signed);\r\n spf=none (mx1.forwardemail.net: example.net does not designate permitted sender hosts) smtp.mailfrom=test@example.net smtp.helo=user.oem.local;\r\n dmarc=none header.from=your-domain.your-domain.your-domain.your-domain.example.com;\r\n bimi=skipped (DMARC not enabled)\r\n",
"headerLines": [
{
"key": "arc-seal",
"line": "ARC-Seal: i=1; a=rsa-sha256; t=1653506802; cv=none; d=forwardemail.net;\r\n s=default;\r\n b=R6QJ0tGwwjg2VPxiAlVIKxsg3jEPtRGKPTIOdZNWuhWrbssttFdOYzRRqvacDyN5SLoyDhVye\r\n DUA/64IxANXdHVFlpR258Yp7WxLDv2gtJD5vNSKYmUJZOWk1TynmlqTYrp0Vuqg2xIUjIlPBWAJ\r\n PPNx4JvOLjJuWYynU2qIWz0="
},
{
"key": "arc-message-signature",
"line": "ARC-Message-Signature: i=1; a=rsa-sha256; c=relaxed/relaxed;\r\n d=forwardemail.net; h=MIME-Version: Date: Message-ID: From: Content-Type;\r\n q=dns/txt; s=default; t=1653506802;\r\n bh=cEYDoyTy+Ub29XZt/zXR+sprfUE6BW0y5cHfah01PT4=;\r\n b=F/t56AAXr2Kv3G6VsbdT5OKDVJf2ulhwLiTM18Ra4tDPUKPSGSLKrWvxiXEg5NMWwdWnsOYrL\r\n r3YSm4uMxVMhHZbHm/sUu4QZq5/18hQsAkCv6fI9ifTjDwBrN5zpLOhPoZFFo+TyvHxiII3Xv3L\r\n UEzmUIIaJRX6tboQ160tino="
},
{
"key": "arc-authentication-results",
"line": "ARC-Authentication-Results: i=1; mx1.forwardemail.net;\r\n dkim=none (message not signed);\r\n spf=none (mx1.forwardemail.net: example.net does not designate permitted sender hosts) smtp.mailfrom=test@example.net smtp.helo=user.oem.local;\r\n dmarc=none header.from=your-domain.your-domain.your-domain.your-domain.example.com;\r\n bimi=skipped (DMARC not enabled)"
},
{
"key": "received-spf",
"line": "Received-SPF: none (mx1.forwardemail.net: example.net does not designate permitted sender hosts) client-ip=127.0.0.1;"
},
{
"key": "authentication-results",
"line": "Authentication-Results: mx1.forwardemail.net;\r\n dkim=none (message not signed);\r\n spf=none (mx1.forwardemail.net: example.net does not designate permitted sender hosts) smtp.mailfrom=test@example.net smtp.helo=user.oem.local;\r\n dmarc=none header.from=your-domain.your-domain.your-domain.your-domain.example.com;\r\n bimi=skipped (DMARC not enabled)"
},
{
"key": "x-forward-email-sender",
"line": "X-Forward-Email-Sender: rfc822; test@example.net"
},
{
"key": "x-forward-email-session-id",
"line": "X-Forward-Email-Session-ID: w2czxgznghn5ryyw"
},
{
"key": "x-forward-email-version",
"line": "X-Forward-Email-Version: 9.0.0"
},
{
"key": "content-type",
"line": "Content-Type: multipart/mixed; boundary=\"--_NmP-179a735428ca7575-Part_1\""
},
{
"key": "from",
"line": "From: some <random@your-domain.your-domain.your-domain.your-domain.example.com>"
},
{
"key": "message-id",
"line": "Message-ID: <69ad5fc2-91cb-728f-ae5c-eeedc5f267b6@example.net>"
},
{
"key": "date",
"line": "Date: Wed, 25 May 2022 19:26:41 +0000"
},
{
"key": "mime-version",
"line": "MIME-Version: 1.0"
}
],
"html": "<strong>some random text</strong>",
"text": "some random text",
"textAsHtml": "<p>some random text</p>",
"date": "2022-05-25T19:26:41.000Z",
"from": {
"value": [
{
"address": "random@your-domain.your-domain.your-domain.your-domain.example.com",
"name": "some"
}
],
"html": "<span class=\"mp_address_group\"><span class=\"mp_address_name\">some</span> <<a href=\"mailto:random@your-domain.your-domain.your-domain.your-domain.example.com\" class=\"mp_address_email\">random@your-domain.your-domain.your-domain.your-domain.example.com</a>></span>",
"text": "some <random@your-domain.your-domain.your-domain.your-domain.example.com>"
},
"messageId": "<69ad5fc2-91cb-728f-ae5c-eeedc5f267b6@example.net>",
"raw": "ARC-Seal: i=1; a=rsa-sha256; t=1653506802; cv=none; d=forwardemail.net;\r\n s=default;\r\n b=R6QJ0tGwwjg2VPxiAlVIKxsg3jEPtRGKPTIOdZNWuhWrbssttFdOYzRRqvacDyN5SLoyDhVye\r\n DUA/64IxANXdHVFlpR258Yp7WxLDv2gtJD5vNSKYmUJZOWk1TynmlqTYrp0Vuqg2xIUjIlPBWAJ\r\n PPNx4JvOLjJuWYynU2qIWz0=\r\nARC-Message-Signature: i=1; a=rsa-sha256; c=relaxed/relaxed;\r\n d=forwardemail.net; h=MIME-Version: Date: Message-ID: From: Content-Type;\r\n q=dns/txt; s=default; t=1653506802;\r\n bh=cEYDoyTy+Ub29XZt/zXR+sprfUE6BW0y5cHfah01PT4=;\r\n b=F/t56AAXr2Kv3G6VsbdT5OKDVJf2ulhwLiTM18Ra4tDPUKPSGSLKrWvxiXEg5NMWwdWnsOYrL\r\n r3YSm4uMxVMhHZbHm/sUu4QZq5/18hQsAkCv6fI9ifTjDwBrN5zpLOhPoZFFo+TyvHxiII3Xv3L\r\n UEzmUIIaJRX6tboQ160tino=\r\nARC-Authentication-Results: i=1; mx1.forwardemail.net;\r\n dkim=none (message not signed);\r\n spf=none (mx1.forwardemail.net: example.net does not designate permitted sender hosts) smtp.mailfrom=test@example.net smtp.helo=user.oem.local;\r\n dmarc=none header.from=your-domain.your-domain.your-domain.your-domain.example.com;\r\n bimi=skipped (DMARC not enabled)\r\nReceived-SPF: none (mx1.forwardemail.net: example.net does not designate permitted sender hosts) client-ip=127.0.0.1;\r\nAuthentication-Results: mx1.forwardemail.net;\r\n dkim=none (message not signed);\r\n spf=none (mx1.forwardemail.net: example.net does not designate permitted sender hosts) smtp.mailfrom=test@example.net smtp.helo=user.oem.local;\r\n dmarc=none header.from=your-domain.your-domain.your-domain.your-domain.example.com;\r\n bimi=skipped (DMARC not enabled)\r\nX-Forward-Email-Sender: rfc822; test@example.net\r\nX-Forward-Email-Session-ID: w2czxgznghn5ryyw\r\nX-Forward-Email-Version: 9.0.0\r\nContent-Type: multipart/mixed; boundary=\"--_NmP-179a735428ca7575-Part_1\"\r\nFrom: some <random@your-domain.your-domain.your-domain.your-domain.example.com>\r\nMessage-ID: <69ad5fc2-91cb-728f-ae5c-eeedc5f267b6@example.net>\r\nDate: Wed, 25 May 2022 19:26:41 +0000\r\nMIME-Version: 1.0\r\n\r\n----_NmP-179a735428ca7575-Part_1\r\nContent-Type: multipart/alternative;\r\n boundary=\"--_NmP-179a735428ca7575-Part_2\"\r\n\r\n----_NmP-179a735428ca7575-Part_2\r\nContent-Type: text/plain; charset=utf-8\r\nContent-Transfer-Encoding: 7bit\r\n\r\nsome random text\r\n----_NmP-179a735428ca7575-Part_2\r\nContent-Type: text/html; charset=utf-8\r\nContent-Transfer-Encoding: 7bit\r\n\r\n<strong>some random text</strong>\r\n----_NmP-179a735428ca7575-Part_2--\r\n\r\n----_NmP-179a735428ca7575-Part_1\r\nContent-Type: text/plain; name=text1.txt\r\nContent-Transfer-Encoding: base64\r\nContent-Disposition: attachment; filename=text1.txt\r\n\r\naGVsbG8gd29ybGQh\r\n----_NmP-179a735428ca7575-Part_1--\r\n",
"dkim": {
"headerFrom": [
"random@your-domain.your-domain.your-domain.your-domain.example.com"
],
"envelopeFrom": "test@example.net",
"results": [
{
"status": {
"result": "none",
"comment": "message not signed"
},
"info": "dkim=none (message not signed)"
}
]
},
"spf": {
"domain": "example.net",
"client-ip": "127.0.0.1",
"helo": "user.oem.local",
"envelope-from": "test@example.net",
"status": {
"result": "none",
"comment": "mx1.forwardemail.net: example.net does not designate permitted sender hosts",
"smtp": {
"mailfrom": "test@example.net",
"helo": "user.oem.local"
}
},
"header": "Received-SPF: none (mx1.forwardemail.net: example.net does not designate permitted sender hosts) client-ip=127.0.0.1;",
"info": "spf=none (mx1.forwardemail.net: example.net does not designate permitted sender hosts) smtp.mailfrom=test@example.net smtp.helo=user.oem.local",
"lookups": {
"limit": 50,
"count": 1
}
},
"arc": {
"status": {
"result": "none"
},
"i": 0,
"authResults": "mx1.forwardemail.net;\r\n dkim=none (message not signed);\r\n spf=none (mx1.forwardemail.net: example.net does not designate permitted sender hosts) smtp.mailfrom=test@example.net smtp.helo=user.oem.local;\r\n dmarc=none header.from=your-domain.your-domain.your-domain.your-domain.example.com;\r\n bimi=skipped (DMARC not enabled)"
},
"dmarc": {
"status": {
"result": "none",
"header": {
"from": "your-domain.your-domain.your-domain.your-domain.example.com"
}
},
"domain": "your-domain.your-domain.your-domain.your-domain.example.com",
"info": "dmarc=none header.from=your-domain.your-domain.your-domain.your-domain.example.com"
},
"bimi": {
"status": {
"header": {},
"result": "skipped",
"comment": "DMARC not enabled"
},
"info": "bimi=skipped (DMARC not enabled)"
},
"recipients": [
"webhook1@webhooks.net"
],
"session": {
"recipient": "webhook1@webhooks.net",
"remoteAddress": "127.0.0.1",
"remotePort": 65138,
"clientHostname": "[127.0.0.1]",
"hostNameAppearsAs": "user.oem.local",
"sender": "test@example.net",
"mta": "mx1.forwardemail.net",
"arrivalDate": "2022-05-25T19:26:41.423Z",
"arrivalTime": 1653506801423
}
}
Do you support regular expressions or regex
Yes, as of September 27, 2021 we have added this feature. You can simply write regular expressions ("regex") for matching aliases and performing substitions.
Regular expression supported aliases are ones that start with a / and end with / and their recipients are email addresses or webhooks. The recipients can also include regex substitution support (e.g. $1, $2).
We support two regular expression flags including i and g. The case-insensitive flag of i is a permanent default and it is always enforced. The global flag of g can be added by you by affixing the ending / with /g.
Note that we also support our disabled alias feature for the recipient portion with our regex support.
Regular expressions are not supported on global vanity domains (as this could be a security vulnerability).
Examples for Enhanced Privacy Protection
| Alias Name | Effect | Test |
|---|---|---|
/^(linus|torvalds)$/ |
Emails to `linus@your-domain.your-domain.your-domain.your-domain.example.com` or `torvalds@your-domain.your-domain.your-domain.your-domain.example.com` | (view test on RegExr) |
/^24highst(reet)$/ |
Emails to `24highst@your-domain.your-domain.your-domain.your-domain.example.com` or `24highstreet@your-domain.your-domain.your-domain.your-domain.example.com` | (view test on RegExr) |
Examples for the free plan
If you are on the free plan, then simply add a new DNS TXT record using one or more of the provided examples below:
| Name/Host/Alias | TTL | Type | Answer/Value |
|---|---|---|---|
| "@", ".", or blank | 3600 | TXT | forward-email=/^(linus|torvalds)$/:user@gmail.com |
| Name/Host/Alias | TTL | Type | Answer/Value |
|---|---|---|---|
| "@", ".", or blank | 3600 | TXT | forward-email=/^([A-Za-z]+)+\.([A-Za-z]+)+$/:$1.$2@company.com |
| Name/Host/Alias | TTL | Type | Answer/Value |
|---|---|---|---|
| "@", ".", or blank | 3600 | TXT | forward-email=/^(support|info)$/:user+$1@gmail.com |
| Name/Host/Alias | TTL | Type | Answer/Value |
|---|---|---|---|
| "@", ".", or blank | 3600 | TXT | forward-email=/^(.*?)$/:https://your-domain.your-domain.your-domain.your-domain.example.com/webhook?username=$1 |
| Name/Host/Alias | TTL | Type | Answer/Value |
|---|---|---|---|
| "@", ".", or blank | 3600 | TXT | forward-email=/^(linus|torvalds)$/:! |
| Name/Host/Alias | TTL | Type | Answer/Value |
|---|---|---|---|
| "@", ".", or blank | 3600 | TXT | forward-email=/^(linus|torvalds)$/:!! |
| Name/Host/Alias | TTL | Type | Answer/Value |
|---|---|---|---|
| "@", ".", or blank | 3600 | TXT | forward-email=/^(linus|torvalds)$/:!!! |
What are your outbound SMTP limits
We rate limit users and domains to 300 outbound SMTP messages per 1 day. This averages 9000+ emails in a calendar month. If you need to exceed this amount or have consistently large emails, then please contact us.
Do I need approval to enable SMTP
Yes, please note that in order to maintain IP reputation and ensure deliverability, Forward Email has a manual review process on a per-domain basis for outbound SMTP approval. Email support@forwardemail.net or open a help request for approval. This typically takes less than 24 hours, with most requests being honored within 1-2 hours. In the near future we aim to make this process instant with additional spam controls and alerting. This process ensures that your emails reach the inbox and your messages don't get marked as spam.
What are your SMTP server configuration settings
Our server is smtp.forwardemail.net and is also monitored on our status page.
It supports both IPv4 and IPv6 and is available over ports 465 and 2465 for SSL/TLS and 587, 2587, 2525, and 25 for TLS (STARTTLS).
As of October 2025, we now support legacy TLS 1.0 connections on ports 2455 (SSL/TLS) and 2555 (STARTTLS) for older devices such as printers, scanners, cameras, and legacy email clients that cannot support modern TLS versions. These ports are provided as an alternative to Gmail, Yahoo, Outlook, and other providers that have discontinued support for older TLS protocols.
Caution
Legacy TLS 1.0 Support (Ports 2455 and 2555): These ports use the deprecated TLS 1.0 protocol which has known security vulnerabilities (BEAST, POODLE). Only use these ports if your device absolutely cannot support TLS 1.2 or higher. We strongly recommend upgrading your device firmware or switching to modern email clients whenever possible. These ports are intended solely for legacy hardware compatibility (old printers, scanners, cameras, IoT devices).
| Protocol | Hostname | Ports | IPv4 | IPv6 | Notes |
|---|---|---|---|---|---|
SSL/TLS Preferred |
smtp.forwardemail.net |
465, 2465 |
✅ | ✅ | Modern TLS 1.2+ (Recommended) |
TLS (STARTTLS) |
smtp.forwardemail.net |
587, 2587, 2525, 25 |
✅ | ✅ | Modern TLS 1.2+ (Recommended) |
SSL/TLS Legacy Only |
smtp.forwardemail.net |
2455 |
✅ | ✅ | ⚠️ TLS 1.0 for old devices only |
TLS (STARTTLS) Legacy Only |
smtp.forwardemail.net |
2555 |
✅ | ✅ | ⚠️ TLS 1.0 for old devices only |
| Login | Example | Description |
|---|---|---|
| Username | user@your-domain.your-domain.your-domain.your-domain.example.com |
Email address of an alias that exists for the domain at My Account Domains. |
| Password | ************************ |
Alias |
In order to send outbound email with SMTP, the SMTP user must be the email address of an alias that exists for the domain at My Account Domains – and the SMTP password must be an alias-specific generated password.
Please refer to Do you support sending email with SMTP for step by step instructions.
What are your IMAP server configuration settings
Our server is imap.forwardemail.net and is also monitored on our status page.
It supports both IPv4 and IPv6 and is available over ports 993 and 2993 for SSL/TLS.
| Protocol | Hostname | Ports | IPv4 | IPv6 |
|---|---|---|---|---|
SSL/TLS Preferred |
imap.forwardemail.net |
993, 2993 |
✅ | ✅ |
| Login | Example | Description |
|---|---|---|
| Username | user@your-domain.your-domain.your-domain.your-domain.example.com |
Email address of an alias that exists for the domain at My Account Domains. |
| Password | ************************ |
Alias-specific generated password. |
In order to connect with IMAP, the IMAP user must be the email address of an alias that exists for the domain at My Account Domains – and the IMAP password must be an alias-specific generated password.
Please refer to Do you support receiving email with IMAP for step by step instructions.
What are your POP3 server configuration settings
Our server is pop3.forwardemail.net and is also monitored on our status page.
It supports both IPv4 and IPv6 and is available over ports 995 and 2995 for SSL/TLS.
| Protocol | Hostname | Ports | IPv4 | IPv6 |
|---|---|---|---|---|
SSL/TLS Preferred |
pop3.forwardemail.net |
995, 2995 |
✅ | ✅ |
| Login | Example | Description |
|---|---|---|
| Username | user@your-domain.your-domain.your-domain.your-domain.example.com |
Email address of an alias that exists for the domain at My Account Domains. |
| Password | ************************ |
Alias-specific generated password. |
In order to connect with POP3, the POP3 user must be the email address of an alias that exists for the domain at My Account Domains – and the IMAP password must be an alias-specific generated password.
Please refer to Do you support POP3 for step by step instructions.
Security
Advanced Server Hardening Techniques
Tip
Learn more about our security infrastructure on our Security page.
Forward Email implements numerous server hardening techniques to ensure the security of our infrastructure and your data:
-
Network Security:
- IP tables firewall with strict rules
- Fail2ban for brute force protection
- Regular security audits and penetration testing
- VPN-only administrative access
-
System Hardening:
- Minimal package installation
- Regular security updates
- SELinux in enforcing mode
- Disabled root SSH access
- Key-based authentication only
-
Application Security:
- Content Security Policy (CSP) headers
- HTTPS Strict Transport Security (HSTS)
- XSS protection headers
- Frame options and referrer policy headers
- Regular dependency audits
-
Data Protection:
- Full disk encryption with LUKS
- Secure key management
- Regular backups with encryption
- Data minimization practices
-
Monitoring and Response:
- Real-time intrusion detection
- Automated security scanning
- Centralized logging and analysis
- Incident response procedures
Important
Our security practices are continuously updated to address emerging threats and vulnerabilities.
Tip
For maximum security, we recommend using our service with end-to-end encryption via OpenPGP.
Do you have SOC 2 or ISO 27001 certifications
Note
Forward Email operates on infrastructure provided by certified subprocessors to ensure compliance with industry standards.
Forward Email does not directly hold SOC 2 Type II or ISO 27001 certifications. However, the service operates on infrastructure provided by certified subprocessors:
-
DigitalOcean: SOC 2 Type II and SOC 3 Type II certified (audited by Schellman & Company LLC), ISO 27001 certified at multiple data centers. Details: https://www.digitalocean.com/trust/certification-reports
-
Vultr: SOC 2+ (HIPAA) certified, ISO/IEC certifications: 20000-1:2018, 27001:2022, 27017:2015, 27018:2019. Details: https://www.vultr.com/legal/compliance/
-
DataPacket: SOC 2 compliant (contact DataPacket directly to obtain certification), enterprise-grade infrastructure provider (Denver location). Details: https://www.datapacket.com/datacenters/denver
Forward Email follows industry best practices for security audits and regularly engages with independent security researchers. Source: https://forwardemail.net/technical-whitepaper.pdf#page=36
Do you use TLS encryption for email forwarding
Yes. Forward Email strictly enforces TLS 1.2+ for all connections (HTTPS, SMTP, IMAP, POP3) and implements MTA-STS for enhanced TLS support. The implementation includes:
- TLS 1.2+ enforcement for all email connections
- ECDHE (Elliptic Curve Diffie-Hellman Ephemeral) key exchange for perfect forward secrecy
- Modern cipher suites with regular security updates
- HTTP/2 support for improved performance and security
- HSTS (HTTP Strict Transport Security) with preloading in major browsers
- MTA-STS (Mail Transfer Agent Strict Transport Security) for strict TLS enforcement
Source: https://forwardemail.net/technical-whitepaper.pdf#page=25
MTA-STS Implementation: Forward Email implements strict MTA-STS enforcement in the codebase. When TLS errors occur and MTA-STS is enforced, the system returns 421 SMTP status codes to ensure emails are retried later rather than being delivered insecurely. Implementation details:
- TLS error detection: https://github.com/forwardemail/forwardemail.net/blob/master/helpers/is-tls-error.js
- MTA-STS enforcement in send-email helper: https://github.com/forwardemail/forwardemail.net/blob/master/helpers/send-email.js
Third-party validation: https://www.hardenize.com/report/forwardemail.net/1750312779 shows "Good" ratings for all TLS and transport security measures.
Do you preserve email authentication headers
Yes. Forward Email comprehensively implements and preserves email authentication headers:
- SPF (Sender Policy Framework): Properly implemented and preserved
- DKIM (DomainKeys Identified Mail): Full support with proper key management
- DMARC: Policy enforcement for emails that fail SPF or DKIM validation
- ARC: While not explicitly detailed, the service's perfect compliance scores suggest comprehensive authentication header handling
Source: https://forwardemail.net/technical-whitepaper.pdf#page=31
Validation: Internet.nl Mail Test shows 100/100 score specifically for "SPF, DKIM, and DMARC" implementation. Hardenize assessment confirms "Good" ratings for SPF and DMARC: https://www.hardenize.com/report/forwardemail.net/1750312779
Do you preserve original email headers and prevent spoofing
Tip
Forward Email implements sophisticated anti-spoofing protection to prevent email abuse.
Forward Email preserves original email headers while implementing comprehensive anti-spoofing protection through the MX codebase:
- Header Preservation: Original authentication headers are maintained during forwarding
- Anti-Spoofing: DMARC policy enforcement prevents header spoofing by rejecting emails that fail SPF or DKIM validation
- Header Injection Prevention: Input validation and sanitization using striptags library
- Advanced Protection: Sophisticated phishing detection with spoofing detection, impersonation prevention, and user notification systems
MX Implementation Details: The core email processing logic is handled by the MX server codebase, specifically:
- Main MX data handler: https://github.com/forwardemail/forwardemail.net/blob/master/helpers/on-data-mx.js
- Arbitrary email filtering (anti-spoofing): https://github.com/forwardemail/forwardemail.net/blob/master/helpers/is-arbitrary.js
The isArbitrary helper implements sophisticated anti-spoofing rules including detection of domain impersonation, blocked phrases, and various phishing patterns.
Source: https://forwardemail.net/technical-whitepaper.pdf#page=32
How do you protect against spam and abuse
Forward Email implements comprehensive multi-layer protection:
- Rate Limiting: Applied to authentication attempts, API endpoints, and SMTP connections
- Resource Isolation: Between users to prevent impact from high-volume users
- DDoS Protection: Multi-layer protection through DataPacket's Shield system and Cloudflare
- Automatic Scaling: Dynamic resource adjustment based on demand
- Abuse Prevention: User-specific abuse prevention checks and hash-based blocking for malicious content
- Email Authentication: SPF, DKIM, DMARC protocols with advanced phishing detection
Sources:
- https://forwardemail.net/technical-whitepaper.pdf#page=18
- https://www.datapacket.com/datacenters/denver (DDoS protection details)
- https://github.com/forwardemail/forwardemail.net/blob/master/helpers/abuse-prevention-by-user-id.js
Do you store email content on disk
Important
Forward Email uses a zero-knowledge architecture that prevents email content from being written to disk.
- Zero-Knowledge Architecture: Individually encrypted SQLite mailboxes mean Forward Email cannot access email content
- In-Memory Processing: Email processing occurs entirely in memory, avoiding disk storage
- No Content Logging: "We do not log or store email content or metadata to disk"
- Sandboxed Encryption: Encryption keys are never stored on disk in plaintext
MX Codebase Evidence: The MX server processes emails entirely in memory without writing content to disk. The main email processing handler demonstrates this in-memory approach: https://github.com/forwardemail/forwardemail.net/blob/master/helpers/on-data-mx.js
Sources:
- https://forwardemail.net/technical-whitepaper.pdf#page=10 (Abstract)
- https://forwardemail.net/technical-whitepaper.pdf#page=59 (Zero-knowledge details)
- https://forwardemail.net/technical-whitepaper.pdf#page=21 (Sandboxed encryption)
Can email content be exposed during system crashes
No. Forward Email implements comprehensive safeguards against crash-related data exposure:
- Core Dumps Disabled: Prevents memory exposure during crashes
- Swap Memory Disabled: Completely disabled to prevent sensitive data extraction from swap files
- In-Memory Architecture: Email content exists only in volatile memory during processing
- Encryption Key Protection: Keys are never stored on disk in plaintext
- Physical Security: LUKS v2 encrypted disks prevent physical access to data
- USB Storage Disabled: Prevents unauthorized data extraction
Error Handling for System Issues: Forward Email uses helper functions isCodeBug and isTimeoutError to ensure that if any database connectivity issues, DNS network/blocklist issues, or upstream connectivity issues occur, the system returns 421 SMTP status codes to ensure emails will be retried later rather than being lost or exposed.
Implementation details:
- Error classification: https://github.com/forwardemail/forwardemail.net/blob/master/helpers/is-code-bug.js
- Timeout error handling in MX processing: https://github.com/forwardemail/forwardemail.net/blob/master/helpers/on-data-mx.js
Source: https://forwardemail.net/technical-whitepaper.pdf#page=15
Who has access to your email infrastructure
Forward Email implements comprehensive access controls for its minimal 2-3 person engineering team access with strict 2FA requirements:
- Role-Based Access Control: For team accounts with resource-based permissions
- Least Privilege Principle: Applied throughout all systems
- Segregation of Duties: Between operational roles
- User Management: Separate deploy and devops users with distinct permissions
- Root Login Disabled: Forces access through properly authenticated accounts
- Strict 2FA: No SMS-based 2FA due to risk of MiTM attacks - only app-based or hardware tokens
- Comprehensive Audit Logging: With sensitive data redaction
- Automated Anomaly Detection: For unusual access patterns
- Regular Security Reviews: Of access logs
- Evil Maid Attack Prevention: USB storage disabled and other physical security measures
Sources:
- https://forwardemail.net/technical-whitepaper.pdf#page=30 (Authorization Controls)
- https://forwardemail.net/technical-whitepaper.pdf#page=30 (Network Security)
- https://forwardemail.net/technical-whitepaper.pdf#page=15 (Evil maid attack prevention)
What infrastructure providers do you use
Important
Forward Email uses multiple infrastructure subprocessors with comprehensive compliance certifications.
Complete details are available on our GDPR compliance page: https://forwardemail.net/gdpr
Primary Infrastructure Subprocessors:
| Provider | Data Privacy Framework Certified | GDPR Compliance Page |
|---|---|---|
| Cloudflare | ✅ Yes | https://www.cloudflare.com/trust-hub/gdpr/ |
| DataPacket | ❌ No | https://www.datapacket.com/privacy-policy |
| DigitalOcean | ❌ No | https://www.digitalocean.com/legal/gdpr |
| Vultr | ❌ No | https://www.vultr.com/legal/eea-gdpr-privacy/ |
Detailed Certifications:
DigitalOcean
- SOC 2 Type II & SOC 3 Type II (audited by Schellman & Company LLC)
- ISO 27001 certified at multiple data centers
- PCI-DSS compliant
- CSA STAR Level 1 certified
- APEC CBPR PRP certified
- Details: https://www.digitalocean.com/trust/certification-reports
Vultr
- SOC 2+ (HIPAA) certified
- PCI Merchant compliant
- CSA STAR Level 1 certified
- ISO/IEC 20000-1:2018, 27001:2022, 27017:2015, 27018:2019
- Details: https://www.vultr.com/legal/compliance/
DataPacket
- SOC 2 compliant (contact DataPacket directly to obtain certification)
- Enterprise-grade infrastructure (Denver location)
- DDoS protection through Shield cybersecurity stack
- 24/7 technical support
- Global network across 58 data centers
- Details: https://www.datapacket.com/datacenters/denver
Payment Processors:
- Stripe: Data Privacy Framework certified - https://stripe.com/legal/privacy-center
- PayPal: Not DPF certified - https://www.paypal.com/uk/legalhub/privacy-full
Do you offer a Data Processing Agreement (DPA)
Yes, Forward Email offers a comprehensive Data Processing Agreement (DPA) that can be signed with our enterprise agreement. A copy of our DPA is available at: https://forwardemail.net/dpa
DPA Details:
- Covers GDPR compliance and EU-US/Swiss-US Privacy Shield frameworks
- Automatically accepted when agreeing to our Terms of Service
- No separate signature required for standard DPA
- Custom DPA arrangements available through Enterprise License
GDPR Compliance Framework: Our DPA details compliance with GDPR as well as international data transfer requirements. Complete information is available at: https://forwardemail.net/gdpr
For enterprise customers requiring custom DPA terms or specific contractual arrangements, these can be addressed through our Enterprise License ($250/month) program.
How do you handle data breach notifications
Note
Forward Email's zero-knowledge architecture significantly limits breach impact.
- Limited Data Exposure: Cannot access encrypted email content due to zero-knowledge architecture
- Minimal Data Collection: Only basic subscriber information and limited IP logs for security
- Subprocessor Frameworks: DigitalOcean and Vultr maintain GDPR-compliant incident response procedures
GDPR Representative Information: Forward Email has appointed GDPR representatives in accordance with Article 27:
EU Representative: Osano International Compliance Services Limited ATTN: LFHC 3 Dublin Landings, North Wall Quay Dublin 1, D01C4E0
UK Representative: Osano UK Compliance LTD ATTN: LFHC 42-46 Fountain Street, Belfast Antrim, BT1 - 5EF
For enterprise customers requiring specific breach notification SLAs, these should be discussed as part of an Enterprise License agreement.
Sources:
Do you offer a test environment
Forward Email's technical documentation does not explicitly describe a dedicated sandbox mode. However, potential testing approaches include:
- Self-Hosting Option: Comprehensive self-hosting capabilities for creating test environments
- API Interface: Potential for programmatic testing of configurations
- Open Source: 100% open-source code allows customers to examine forwarding logic
- Multiple Domains: Support for multiple domains could enable test domain creation
For enterprise customers requiring formal sandbox capabilities, this should be discussed as part of an Enterprise License arrangement.
Source: https://github.com/forwardemail/forwardemail.net (Development environment details)
Do you provide monitoring and alerting tools
Forward Email provides real-time monitoring with some limitations:
Available:
- Real-Time Delivery Monitoring: Publicly visible performance metrics for major email providers
- Automatic Alerting: Engineering team alerted when delivery times exceed 10 seconds
- Transparent Monitoring: 100% open-source monitoring systems
- Infrastructure Monitoring: Automated anomaly detection and comprehensive audit logging
Limitations:
- Customer-facing webhooks or API-based delivery status notifications are not explicitly documented
For enterprise customers requiring detailed delivery status webhooks or custom monitoring integrations, these capabilities may be available through Enterprise License arrangements.
Sources:
- https://forwardemail.net (Real-time monitoring display)
- https://github.com/forwardemail/forwardemail.net (Monitoring implementation)
How do you ensure high availability
Important
Forward Email implements comprehensive redundancy across multiple infrastructure providers.
- Distributed Infrastructure: Multiple providers (DigitalOcean, Vultr, DataPacket) across geographic regions
- Geographic Load Balancing: Cloudflare-based geo-located load balancing with automatic failover
- Automatic Scaling: Dynamic resource adjustment based on demand
- Multi-Layer DDoS Protection: Through DataPacket's Shield system and Cloudflare
- Server Redundancy: Multiple servers per region with automatic failover
- Database Replication: Real-time data synchronization across multiple locations
- Monitoring and Alerting: 24/7 monitoring with automatic incident response
Uptime Commitment: 99.9%+ service availability with transparent monitoring available at https://forwardemail.net
Sources:
- https://forwardemail.net/technical-whitepaper.pdf#page=18
- https://www.datapacket.com/datacenters/denver
Are you compliant with Section 889 of the National Defense Authorization Act (NDAA)
Important
Forward Email is fully compliant with Section 889 through careful selection of infrastructure partners.
Yes, Forward Email is Section 889 compliant. Section 889 of the National Defense Authorization Act (NDAA) prohibits government agencies from using or contracting with entities that use telecommunications and video surveillance equipment from specific companies (Huawei, ZTE, Hikvision, Dahua, and Hytera).
How Forward Email Achieves Section 889 Compliance:
Forward Email relies exclusively on two key infrastructure providers, neither of which uses Section 889 prohibited equipment:
- Cloudflare: Our primary partner for network services and email security
- DataPacket: Our primary provider for server infrastructure (using Arista Networks and Cisco equipment exclusively)
- Backup Providers: Our backup providers of Digital Ocean and Vultr are additionally confirmed in writing as being Section 889 compliant.
Cloudflare's Commitment: Cloudflare explicitly states in their Third Party Code of Conduct that they do not use telecommunications equipment, video surveillance products, or services from any Section 889 prohibited entities.
Government Use Case: Our Section 889 compliance was validated when the US Naval Academy selected Forward Email for their secure email forwarding needs, requiring documentation of our federal compliance standards.
For complete details about our government compliance framework, including broader federal regulations, read our comprehensive case study: Federal Government Email Service Section 889 Compliant
System and Technical Details
Do you store emails and their contents
No, we do not write to disk or store logs – with the exception of errors and outbound SMTP (see our Privacy Policy).
Everything is done in-memory and our source code is on GitHub.
How does your email forwarding system work
Email relies on the SMTP protocol. This protocol consists of commands sent to a server (running most commonly on port 25). There is an initial connection, then the sender indicates who the mail is from ("MAIL FROM"), followed by where it's going to ("RCPT TO"), and finally the headers and the body of the email itself ("DATA"). The flow of our email forwarding system is described relative to each SMTP protocol command below:
-
Initial Connection (no command name, e.g.
telnet your-domain.your-domain.your-domain.your-domain.example.com 25) - This is the initial connection. We check senders that aren't in our allowlist against our denylist. Finally, if a sender is not in our allowlist, then we check to see if they have been greylisted. -
HELO- This indicates a greeting to identify the sender's FQDN, IP address, or mail handler name. This value can be spoofed, so we do not rely on this data and instead use the reverse hostname lookup of the connection's IP address. -
MAIL FROM- This indicates the envelope mail from address of the email. If a value is entered, it must be a valid RFC 5322 email address. Empty values are permitted. We check for backscatter here, and we also check the MAIL FROM against our denylist. We finally check senders that are not on the allowlist for rate limiting (see the section on Rate Limiting and allowlist for more information). -
RCPT TO- This indicates the recipient(s) of the email. These must be valid RFC 5322 email addresses. We only permit up to 50 envelope recipients per message (this is different than the "To" header from an email). We also check for a valid Sender Rewriting Scheme ("SRS") address here to protect against spoofing with our SRS domain name. -
DATA- This is the core part of our service which processes an email. See the section How do you process an email for forwarding below for more insight.
How do you process an email for forwarding
This section describes our process related to the SMTP protocol command DATA in the section How does your email forwarding system work above – it is how we process an email's headers, body, security, determine where it needs to be delivered to, and how we handle connections.
-
If the message exceeds the maximum size of 50mb, then it is rejected with a 552 error code.
-
If the message did not contain a "From" header, or if any of the values in the "From" header were not valid RFC 5322 email addresses, then it is rejected with a 550 error code.
-
If the message had more than 25 "Received" headers, then it was determined to have been stuck in a redirect loop, and it is rejected with a 550 error code.
-
Using the email's fingerprint (see the section on Fingerprinting), we will check to see the message has been attempted to be retried for more than 5 days (which matches default postfix behavior), and if so, then it will be rejected with a 550 error code.
-
We store in-memory the results from scanning the email using Spam Scanner.
-
If there were any arbitrary results from Spam Scanner, then it is rejected with a 554 error code. Arbitrary results only include the GTUBE test at the time of this writing. See https://spamassassin.apache.org/gtube/ for more insight.
-
We will add the following headers to the message for debugging and abuse prevention purposes:
Received- we add this standard Received header with origin IP and host, transmission type, TLS connection information, date/time, and recipient.X-Original-To- the original recipient for the message:- This is useful for determining where an email was originally delivered to (in addition to the "Received" header).
- This is added on a per recipient basis at the time of IMAP and/or masked forwarding (in order to protect privacy).
X-Forward-Email-Website- contains a link to our website of https://forwardemail.netX-Forward-Email-Version- the current SemVer version frompackage.jsonof our codebase.X-Forward-Email-Session-ID- a session ID value used for debug purposes (only applies in non-production environments).X-Forward-Email-Sender- a comma separated list containing the original envelope MAIL FROM address (if it was not blank), the reverse PTR client FQDN (if it exists), and the sender's IP address.X-Forward-Email-ID- this is only applicable for outbound SMTP and correlates to the email ID stored in My Account → EmailsX-Report-Abuse- with a value ofabuse@forwardemail.net.X-Report-Abuse-To- with a value ofabuse@forwardemail.net.X-Complaints-To- with a value ofabuse@forwardemail.net.
-
We then check the message for DKIM, SPF, ARC, and DMARC.
- If the message failed DMARC and the domain had a rejection policy (e.g.
p=rejectwas in the DMARC policy), then it is rejected with a 550 error code. Typically a DMARC policy for a domain can be found in the_dmarcsub-domain TXT record, (e.g.dig _dmarc.your-domain.your-domain.your-domain.your-domain.example.com txt). - If the message failed SPF and the domain had a hard fail policy (e.g.
-allwas in the SPF policy as opposed to~allor no policy at all), then it is rejected with a 550 error code. Typically an SPF policy for a domain can be found in the TXT record for the root domain (e.g.dig your-domain.your-domain.your-domain.your-domain.example.com txt). See this section for more information on sending mail as with Gmail regarding SPF.
- If the message failed DMARC and the domain had a rejection policy (e.g.
-
Now we process the recipients of the message as collected from the
RCPT TOcommand in the section How does your email forwarding system work above. For each recipient, we perform the following operations:- We lookup the TXT records of the domain name (the part after the
@symbol, e.g.your-domain.your-domain.your-domain.your-domain.example.comif the email address wastest@your-domain.your-domain.your-domain.your-domain.example.com). For example, if the domain isyour-domain.your-domain.your-domain.your-domain.example.comwe do a DNS lookup such asdig your-domain.your-domain.your-domain.your-domain.example.com txt. - We parse all TXT records that start with either
forward-email=(free plans) orforward-email-site-verification=(paid plans). Note that we parse both, in order to process emails while a user is upgrading or downgrading plans. - From these parsed TXT records, we iterate over them to extract the forwarding configuration (as described in the section How do I get started and set up email forwarding above). Note that we only support one
forward-email-site-verification=value, and if more than one is supplied, then a 550 error will occur and the sender will receive a bounce for this recipient. - Recursively we iterate over the extracted forwarding configuration to determine global forwarding, regex based forwarding, and all other supported forwarding configurations – which are now known as our "Forwarding Addresses".
- For each Forwarding Address, we support one recursive lookup (which will start this series of operations over on the given address). If a recursive match was found, then the parent result will be removed from Forwarding Addresses, and the children added.
- Forwarding Addresses are parsed for uniqueness (since we don't want to send duplicates to one address or spawn additionally unnecessary SMTP client connections).
- For each Forwarding Address, we lookup its domain name against our API endpoint
/v1/max-forwarded-addresses(in order to determine how many addresses the domain is permitted to forward email to per alias, e.g. 10 by default – see the section on maximum limit on forwarding per alias). If this limit is exceeded, then a 550 error will occur and the sender will receive a bounce for this recipient. - We lookup the settings of the original recipient against our API endpoint
/v1/settings, which supports a lookup for paid users (with a fallback for free users). This returns a configuration object for advanced settings forport(Number, e.g.25),has_adult_content_protection(Boolean),has_phishing_protection(Boolean),has_executable_protection(Boolean), andhas_virus_protection(Boolean). - Based off these settings, we then check against Spam Scanner results and if any errors occur, then the message is rejected with a 554 error code (e.g. if
has_virus_protectionis enabled, then we will check the Spam Scanner results for viruses). Note that all free plan users will be opted-in for checks against adult-content, phishing, executables, and viruses. By default, all paid plan users are opted-in as well, but this configuration can be altered under the Settings page for a domain in the Forward Email dashboard).
- We lookup the TXT records of the domain name (the part after the
-
For each processed recipient's Forwarding Addresses, we then perform the following operations:
- The address is checked against our denylist, and if it was listed, then a 421 error code will occur (indicates to sender to retry again later).
- If the address is a webhook, then we set a Boolean for future operations (see below – we group together similar webhooks to make one POST request vs. multiple for delivery).
- If the address is an email address, then we parse the host for future operations (see below – we group together similar hosts to make one connection vs. multiple individual connections for delivery).
-
If there are no recipients and there are no bounces, then we respond with a 550 error of "Invalid recipients".
-
If there are recipients, then we iterate over them (grouped together by the same host) and deliver the emails. See the section How do you handle email delivery issues below for more insight.
- If any errors occur while sending emails, then we will store them in-memory for later processing.
- We will take the lowest error code (if any) from sending emails – and use that as the response code to the
DATAcommand. This means that emails not delivered will typically be retried by the original sender, yet emails that were already delivered will not be re-sent the next time the message is sent (as we use Fingerprinting). - If no errors occurred, then we will send a 250 successful SMTP response status code.
- A bounce is determined to be any delivery attempted that results in a status code that is >= 500 (permanent failures).
-
If no bounces occurred (permanent failures), then we will return a SMTP response status code of the lowest error code from non-permanent failures (or a 250 successful status code if there were none).
-
If bounces did occur then we will send bounce emails in the background after returning the lowest of all error codes to the sender. However, if the lowest error code is >= 500, then we do not send any bounce emails. This is because if we did, then senders would receive a double bounce email (e.g. one from their outbound MTA, such as Gmail – and also one from us). See the section on How do you protect against backscatter below for more insight.
How do you handle email delivery issues
Note that we will do a "Friendly-From" rewrite on the emails if and only if the DMARC policy of the sender was not passing AND no DKIM signatures were aligned with the "From" header. This means that we will alter the "From" header on the message, set "X-Original-From", and also set a "Reply-To" if it was not already set. We will also re-seal the ARC seal on the message after altering these headers.
We also use smart-parsing of error messages at every level of our stack – in our code, DNS requests, Node.js internals, HTTP requests (e.g. 408, 413, and 429 are mapped to the SMTP response code of 421 if the recipient is a webhook), and mail server responses (e.g. responses with "defer" or "slowdown" would be retried as 421 errors).
Our logic is dummy-proof and it will also retry for SSL/TLS errors, connection issues, and more. The goal with dummy-proofing is to maximize deliverability to all recipients for a forwarding configuration.
If the recipient is a webhook, then we will permit a 60 second timeout for the request to complete with up to 3 retries (so 4 requests total before a failure). Note that we correctly parse error codes 408, 413, and 429 and map them to a SMTP response code of 421.
Otherwise if the recipient is an email address, then we will attempt to send the email with opportunistic TLS (we attempt to use STARTTLS if it is available on the recipient mail server). If a SSL/TLS error occurs while attempting to send the email, then we will attempt to send the email without TLS (without using STARTTLS).
If any DNS or connection errors occur, then we will return to the DATA command a SMTP response code of 421, otherwise if there are >= 500 level errors, then bounces will be sent.
If we detect that an email server we are attempting to deliver to has one or more of our mail exchange IP addresses blocked (e.g. by whatever technology they use for deferring spammers), then we will send a SMTP response code of 421 for the sender to retry their message later (and we are alerted to the issue so we can hopefully resolve it before the next attempt).
How do you handle your IP addresses becoming blocked
We routinely monitor all major DNS denylists and if any of our mail exchange ("MX") IP addresses are listed in a major denylist, we will pull it out of the relevant DNS A record round robin if possible until it the issue is resolved.
At the time of this writing, we are listed in several DNS allowlists as well, and we take monitoring denylists seriously. If you see any issues before we have a chance to resolve them, please notify us in writing at support@forwardemail.net.
Our IP addresses are publicly available, see this section below for more insight.
What are postmaster addresses
In order to prevent misdirected bounces and sending vacation responder messages to unmonitored or nonexistent mailboxes, we maintain a list of mailer-daemon like usernames:
automailerautoresponderbouncebounce-notificationbounce-notificationsbounceshostmasterlistservlocalhostmail-daemonmail.daemonmaildaemonmailer-daemonmailer.daemonmailerdaemonmajordomopostmaster- and any no-reply address
See RFC 5320 Section 4.6 for more insight into how lists such as these are used to create efficient email systems.
What are no-reply addresses
Email usernames equal to any of the following (case-insensitive) are considered to be no-reply addresses:
do-not-replydo-not-responddo.not.replydonotreplydonotresponddont-replynaorespondano-repliesno-replyno-replysno.repliesno.replyno.replysno_replynobodynorepliesnoreplynoreplys
This list is maintained as an open-source project on GitHub.
What are your server's IP addresses
We publish our IP addresses at https://forwardemail.net/ips.
Do you have an allowlist
Yes, we have a list of domain name extensions that are allowlisted by default and a dynamic, cached, and rolling allowlist based off strict criteria.
All domains, emails, and IP addresses used by paying customers are automatically checked against our denylist hourly – which alerts admins who can manually intervene if necessary.
Additionally, if one of your domains or its email addresses are denylisted (e.g. for sending spam, viruses, or due to impersonation attacks) – then the domain admins (you) and our team admins will be notified by email immediately. We strongly recommend that you configure DMARC to prevent this.
What domain name extensions are allowlisted by default
The following domain name extensions are considered to be allowlisted by default (regardless if they are on the Umbrella Popularity List or not):
edugovmilintarpadni.usfed.usisa.uskids.usnsn.usak.usal.usar.usas.usaz.usca.usco.usct.usdc.usde.usfl.usga.usgu.ushi.usia.usid.usil.usin.usks.usky.usla.usma.usmd.usme.usmi.usmn.usmo.usms.usmt.usnc.usnd.usne.usnh.usnj.usnm.usnv.usny.usoh.usok.usor.uspa.uspr.usri.ussc.ussd.ustn.ustx.usut.usva.usvi.usvt.uswa.uswi.uswv.uswy.usmil.ttedu.ttedu.tredu.uaedu.auac.atedu.brac.nzschool.nzcri.nzhealth.nzmil.nzparliament.nzac.inedu.inmil.inac.jped.jplg.jpac.zaedu.zamil.zaschool.zamil.krac.krhs.krms.kres.krsc.krkg.kredu.esac.lksch.lkedu.lkac.thmi.thadmin.chcanada.cagc.cago.idgo.jpgo.kego.krgo.thgob.argob.clgob.esgob.mxgob.vegob.svgouv.frgouv.ncgouv.qc.cagov.adgov.afgov.aigov.algov.amgov.aogov.augov.awgov.axgov.azgov.bdgov.begov.bggov.bmgov.bygov.clgov.cngov.cogov.cygov.czgov.dzgov.eggov.figov.fkgov.gggov.grgov.hkgov.hrgov.hugov.iegov.ilgov.imgov.ingov.iqgov.irgov.itgov.jegov.kpgov.krdgov.kygov.kzgov.lbgov.lkgov.ltgov.lvgov.magov.mmgov.mogov.mtgov.mygov.nggov.npgov.phgov.pkgov.plgov.ptgov.pygov.rogov.rugov.scotgov.segov.sggov.sigov.skgov.trgov.ttgov.twgov.uagov.ukgov.vngov.walesgov.zagovernment.pngovt.nzgv.atac.ukbl.ukjudiciary.ukmod.uknhs.ukparliament.ukpolice.ukrct.ukroyal.uksch.ukukaea.uk
Additionally these brand and corporate top-level domains are allowlisted by default (e.g. apple for applecard.apple for Apple Card bank statements):
aaaaarpabarthabbabbottabbvieabcaccentureacoaegaetnaaflagakhanaigaigoairbusairtelakdnalfaromeoalibabaalipayallfinanzallstateallyalstomamazonamericanexpressamexamicaandroidanzaolappleaquarellearamcoaudiauspostawsaxaazurebaidubananarepublicbarclaycardbarclaysbasketballbauhausbbcbbtbbvabcgbentleybhartibingblancobloombergbmsbmwbnlbnpparibasboehringerbondbookingboschbostikbradescobridgestonebrotherbugatticalcalvinkleincanoncapitalonecaravancartiercbacbncbrecbscerncfachanelchasechintaichromechryslerciprianiciscocitadelciticiticclubmedcomcastcommbankcreditunioncrowncrscsccuisinelladaburdatsundealerdelldeloittedeltadhldiscoverdishdnpdodgedunlopdupontdvagedekaemerckepsonericssonerniesuranceetisalateurovisioneverbankextraspacefagefairwindsfarmersfedexferrariferrerofiatfidelityfirestonefirmdaleflickrflirflsmidthfordfoxfreseniusforexfrogansfrontierfujitsufujixeroxgallogallupgapgbizgeagentinggivinggleglobogmailgmogmxgodaddygoldpointgoodyeargooggooglegraingerguardianguccihbohdfchdfcbankhermeshisamitsuhitachihkthondahoneywellhotmailhsbchugheshyatthyundaiibmieeeifmikanoimdbinfinitiintelintuitipirangaiselectitauitvivecojaguarjavajcbjcpjeepjpmorganjuniperkddikerryhotelskerrylogisticskerrypropertieskfhkiakinderkindlekomatsukpmgkredkuokgrouplacaixaladbrokeslamborghinilancasterlancialancomelandroverlanxesslasallelatrobeldsleclerclegoliaisonlexuslidllifestylelillylincolnlindelipsylixillocuslottelpllplfinanciallundbecklupinmacysmaifmanmangomarriottmaseratimattelmckinseymetlifemicrosoftminimitmitsubishimlbmmamonashmormonmotomovistarmsdmtnmtrmutualnadexnationwidenaturanbanecnetflixneustarnewhollandnflnhkniconikenikonnissannissaynokianorthwesternmutualnortonnranttobiofficeomegaoracleorangeotsukapanasonicpccwpfizerphilipspiagetpictetpingpioneerplayplaystationpohlpolitiepraxiprodprogressivepruprudentialpwcqvcredstonereliancerexrothricohrmitrocherrogersrwesafetysakurasamsungsandviksandvikcoromantsanofisapsaxosbiscascbschaefflerschmidtschwarzscjohnsonscorseatsenersessewsevensfrseekshangrilasharpshawshellshriramsinaskyskypesmartsncfsoftbanksohusonyspiegelstadastaplesstarstarhubstatebankstatefarmstatoilstcstcgroupsuzukiswatchswiftcoversymantectaobaotargettatamotorstdktelecitytelefonicatemasektevatiffanytjxtoraytoshibatotaltoyotatravelchanneltravelerstuitvsubsunicomuolupsvanguardverisignvigvikingvirginvisavistavistaprintvivovolkswagenvolvowalmartwalterweatherchannelweberweirwilliamhillwindowswmewolterskluwerwoodsidewtcxboxxeroxxfinityyahooyamaxunyandexyodobashiyoutubezapposzarazippo
As of March 18, 2025 we have also added these French overseas territories to this list (per this GitHub request):
bzhgfgpmqncpfpmretfwfyt
As of July 8, 2025 we have added these Europe-specific countries:
axbgfogigrhrhultlumcmkmtroskva
In October 2025 we have also added cz (Czech Republic) due to demand.
We specifically did not include ru and ua due to high spam activity.
What is your allowlist criteria
We have a static list of domain name extensions allowlisted by default – and we also maintain a dynamic, cached, rolling allowlist based off the following strict criteria:
- Sender root domain must be of a domain name extension that matches the list we offer on our free plan (with the addition of
bizandinfo). We also includeedu,gov, andmilpartial matches, such asxyz.gov.auandxyz.edu.au. - Sender root domain must be within top 100,000 unique root domain parsed results from Umbrella Popularity List ("UPL").
- Sender root domain must be within top 50,000 results from unique root domains appearing in at least 4 of past 7 days of UPL's (~50%+).
- Sender root domain must not be categorized as adult-content or malware by Cloudflare.
- Sender root domain must have either A or MX records set.
- Sender root domain must have either A record(s), MX record(s), DMARC record with
p=rejectorp=quarantine, or an SPF record with-allor~allqualifier.
If this criteria is satisfied, then the sender root domain will be cached for 7 days. Note that our automated job runs daily – therefore this is a rolling allowlist cache that updates daily.
Our automated job will download the previous 7 days of UPL's in-memory, unzip them, and then parse in-memory according to the strict criteria above.
Popular domains at the time of this writing such as Google, Yahoo, Microsoft, Amazon, Meta, Twitter, Netflix, Spotify, and more – are of course included.
If you are a sender not in our allowlist, then the first time your FQDN root domain or IP address sends an email, you will be rate limited and greylisted. Note that this is standard practice adopted as an email standard. Most email server clients will attempt to retry if they receive a rate limit or greylist error (e.g. a 421 or 4xx level error status code).
Note that specific senders such as a@gmail.com, b@xyz.edu, and c@gov.au can still be denylisted (e.g. if we automatically detect spam, phishing, or malware from those senders).
What domain name extensions can be used for free
As of March 31, 2023 we enforced a new blanket spam rule to protect our users and service.
This new rule allows only the following domain name extensions to be used on our free plan:
acadagaialamappasatauaxbabebgbrbybzhcacatcccdchckcocomdedevdjdkeeeseufamilyfifmfofrgfgggiglgpgrhrhuidieiliminioirisitjejpkekrlaliltlulvlymcmdmemkmnmqmsmtmumxncnetninlnonunzorgpfplpmprptpwrerorsscseshsisksmsrsttctftmtotvukusuzvavcvgvuwfwsxyzytza
Do you have a greylist
Yes, we have a very lax email greylisting policy used. Greylisting only applies for senders not on our allowlist and lasts in our cache for 30 days.
For any new sender, we store a key in our Redis database for 30 days with a value set to the initial arrival time of their first request. We then reject their email with a retry status code of 450 and only allow it to pass once 5 minutes has passed.
If they have successfully waited for 5 minutes from this initial arrival time, then their emails will be accepted and they will not receive this 450 status code.
The key consists of either the FQDN root domain or the sender's IP address. This means that any sub-domain that passes the greylist also will pass for the root domain, and vice-versa (this is what we mean by a "very lax" policy).
For example, if an email comes from test.your-domain.your-domain.your-domain.your-domain.example.com before we see an email come from your-domain.your-domain.your-domain.your-domain.example.com, then any email from test.your-domain.your-domain.your-domain.your-domain.example.com and/or your-domain.your-domain.your-domain.your-domain.example.com will have to wait 5 minutes from the initial arrival time of the connection. We do not make both test.your-domain.your-domain.your-domain.your-domain.example.com and your-domain.your-domain.your-domain.your-domain.example.com each wait their own 5 minute periods (our greylisting policy applies at the root domain level).
Note that greylisting does not apply to any sender on our allowlist (e.g. Meta, Amazon, Netflix, Google, Microsoft at the time of this writing).
Do you have a denylist
Yes, we operate our own denylist and update it automatically in real-time and manually based off spam and malicious activity detected.
We also pull all IP addresses from the UCEPROTECT Level 1 denylist at http://wget-mirrors.uceprotect.net/rbldnsd-all/dnsbl-1.uceprotect.net.gz every hour and feed it into our denylist with a 7 day expiry.
Senders found in the denylist will receive a 421 error code (indicates to sender to retry again later) if they are not allowlisted.
By using a 421 status code instead of a 554 status code, potential false positives can be alleviated in real-time and then the message can be successfully delivered on the next attempt.
This is designed unlike other mail services, where if you are put on a blocklist, a hard and permanent failure occurs. It is often difficult to ask senders to retry messages (especially from large organizations), and therefore this approach gives roughly 5 days from the initial email attempt for either the sender, recipient, or us to step in and alleviate the issue (by requesting denylist removal).
All denylist removal requests are monitored in real-time by admins (e.g. so that recurring false positives can be permanently allowlisted by admins).
Denylist removal requests can be requested at https://forwardemail.net/denylist. Paid users have their denylist removal requests instantly processed, while non-paid users must wait for admins to process their request.
Senders that are detected to be sending spam or virus content will be added to the denylist in the following approach:
- The initial message fingerprint is greylisted upon detection of spam or blocklist from a "trusted" sender (e.g.
gmail.com,microsoft.com,apple.com).- If the sender was allowlisted, the message is greylisted for 1 hour.
- If the sender is not allowlisted, the message is greylisted for 6 hours.
- We parse denylist keys from information from the sender and message, and for each of these keys we create (if one does not already exist) a counter, increment it by 1, and cache it for 24 hours.
- For allowlisted senders:
- Add a key for the envelope "MAIL FROM" email address if it had passing SPF or no SPF, and it was not a postmaster username or a no-reply username.
- If "From" header was allowlisted, then add a key for the "From" header email address if it had passing SPF or passing and aligned DKIM.
- If "From" header was not allowlisted, then add a key for the "From" header email address and its root parsed domain name.
- For non-allowlisted senders:
- Add a key for the envelope "MAIL FROM" email address if it had passing SPF.
- If "From" header was allowlisted, then add a key for the "From" header email address if it had passing SPF or passing and aligned DKIM.
- If "From" header was not allowlisted, then add a key for the "From" header email address and its root parsed domain name.
- Add a key for the remote IP address of the sender.
- Add a key for the client resolved hostname by reverse lookup from the IP address of the sender (if any).
- Add a key for the root domain of the client resolved hostname (if any, and if it differs than the client resolved hostname).
- For allowlisted senders:
- If the counter reaches 5 for a non-allowlisted sender and key, then we denylist the key for 30 days and an email is sent to our abuse team. These numbers may change and updates will be reflected here as we monitor abuse.
- If the counter reaches 10 for an allowlisted sender and key, then we denylist the key for 7 days and an email is sent to our abuse team. These numbers may change and updates will be reflected here as we monitor abuse.
NOTE: In the near future we will introduce reputation monitoring. Reputation monitoring will instead calculate when to denylist a sender based off a percentage threshold (as opposed to a rudimentary counter as noted above).
Do you have rate limiting
Sender rate limiting is either by the root domain parsed from a reverse PTR lookup on the sender's IP address – or if that does not yield a result, then it simply uses the sender's IP address. Note that we refer to this as Sender below.
Our MX servers have daily limits for inbound mail received for encrypted IMAP storage:
- Instead of rate limiting inbound mail received on an individual alias basis (e.g.
you@yourdomain.com) – we rate limit by the alias's domain name itself (e.g.yourdomain.com). This preventsSendersfrom flooding the inboxes of all aliases across your domain at once. - We have general limits that apply to all
Sendersacross our service regardless of recipient:Sendersthat we consider to be "trusted" as a source of truth (e.g.gmail.com,microsoft.com,apple.com) are limited to sending 100 GB per day.Sendersthat are allowlisted are limited to sending 10 GB per day.- All other
Sendersare limited to sending 1 GB and/or 1000 messages per day.
- We have a specific limit per
Senderandyourdomain.comof 1 GB and/or 1000 messages daily.
The MX servers also limit messages being forwarded to one or more recipients through rate limiting – but this only applies to Senders not on the allowlist:
-
We only permit up to 100 connections per hour, per
Senderresolved FQDN root domain (or)Senderremote IP address (if no reverse PTR is available), and per envelope recipient to. We store the key for rate limiting as a cryptographic hash in our Redis database. -
If you are sending email through our system, please ensure you have a reverse PTR set up for all your IP addresses (otherwise each unique FQDN root domain or IP address you send from will be rate limited).
-
Note that if you send through a popular system such as Amazon SES, then you will not be rate limited since (at the time of this writing) Amazon SES is listed in our allowlist.
-
If you are sending from a domain such as
test.abc.123.your-domain.your-domain.your-domain.your-domain.example.com, then the rate limit will be imposed onyour-domain.your-domain.your-domain.your-domain.example.com. Many spammers use hundreds of sub-domains to work around common spam filters that only rate limit unique hostnames as opposed to unique FQDN root domains. -
Sendersthat exceed the rate limit will be rejected with a 421 error.
Our IMAP and SMTP servers limit your aliases from having more than 60 concurrent connections at once.
Our MX servers limit non-allowlisted senders from establishing more than 10 concurrent connections (with 3 minute cache expiry for the counter, which mirrors our socket timeout of 3 minutes).
How do you protect against backscatter
Misdirected bounces or bounce spam (known as "Backscatter") can cause negative reputation to sender IP addreses.
We take two steps to protect against backscatter, which is detailed in the following sections Prevent bounces from known MAIL FROM spammers and Prevent unnecessary bounces to protect against backscatter below.
Prevent bounces from known MAIL FROM spammers
We pull the list from Backscatter.org (powered by UCEPROTECT) at http://wget-mirrors.uceprotect.net/rbldnsd-all/ips.backscatterer.org.gz every hour and feed it into our Redis database (we also compare the difference in advance; in case any IP's were removed that need to be honored).
If the MAIL FROM is blank OR is equal to (case-insensitive) any of the postmaster addresses (the portion before the @ in an email), then we check to see if the sender IP matches one from this list.
If the sender's IP is listed (and not in our allowlist), then we send a 554 error with the message The IP ${session.remoteAddress} is blocked by https://www.backscatterer.org/index.php?target=test&ip=${session.remoteAddress}. We will be alerted if a sender is on both the Backscatterer list and in our allowlist so we can resolve the issue if necessary.
The techniques described in this section adhere to the "SAFE MODE" recommendation at https://www.backscatterer.org/?target=usage – where we only check the sender IP if certain conditions have already been met.
Prevent unnecessary bounces to protect against backscatter
Bounces are emails that indicate email forwarding completely failed to the recipient and the email will not be retried.
A common reason for getting listed on the Backscatterer list is misdirected bounces or bounce spam, so we must protect against this in a few ways:
-
We only send when >= 500 status code errors occur (when emails attempted to be forwarded have failed, e.g. Gmail responds with a 500 level error).
-
We only send once and once only (we use a calculated bounce fingerprint key and store it in cache to prevent sending duplicates). The bounce fingerprint is a key that is the message's fingerprint combined with a hash of the bounce address and its error code). See the section on Fingerprinting for more insight into how the message fingerprint is calculated. Successfully sent bounce fingerprints will expire after 7 days in our Redis cache.
-
We only send when the MAIL FROM and/or From is not blank and does not contain (case-insensitive) a postmaster username (the portion before the @ in an email).
-
We don't send if the original message had any of the following headers (case-insensitive):
- Header of
auto-submittedwith a value not equal tono. - Header of
x-auto-response-suppresswith a value ofdr,autoreply,auto-reply,auto_reply, orall - Header of
list-id,list-subscribe,list-unsubscribe,list-help,list-post,list-owner,list-archive,x-autoreply,x-autorespond, orx-auto-respond(regardless of value). - Header of
precedencewith a value ofbulk,autoreply,auto-reply,auto_reply, orlist.
- Header of
-
We don't send if the MAIL FROM or From email address ends with
+donotreply,-donotreply,+noreply, or-noreply. -
We don't send if the From email address username portion was
mdaemonand it had a case-insensitive header ofX-MDDSN-Message. -
We don't send if there was a case-insensitive
content-typeheader ofmultipart/report.
How do you determine an email fingerprint
An email's fingerprint is used for determining uniqueness of an email and to prevent duplicate messages from being delivered and duplicate bounces from being sent.
The fingerprint is calculated from the following list:
- Client resolved FQDN hostname or IP address
Message-IDheader value (if any)Dateheader value (if any)Fromheader value (if any)Toheader value (if any)Ccheader value (if any)Subjectheader value (if any)Bodyvalue (if any)
Can I forward emails to ports other than 25 (e.g. if my ISP has blocked port 25)
Yes, as of May 5, 2020 we have added this feature. Right now the feature is domain-specific, as opposed to alias-specific. If you require it to be alias-specific, please contact us to let us know of your needs.
If you are on the free plan, then simply add a new DNS TXT record as shown below, but change the port from 25 to the port of your choosing.
For example, if I want all emails that go to your-domain.your-domain.your-domain.your-domain.example.com to forward to alias recipients' SMTP port of 1337 instead of 25:
| Name/Host/Alias | TTL | Type | Answer/Value |
|---|---|---|---|
| "@", ".", or blank | 3600 | TXT | forward-email-port=1337 |
| Name/Host/Alias | TTL | Type | Answer/Value |
|---|---|---|---|
| "@", ".", or blank | 3600 | TXT | forward-email=your-domain.your-domain.your-domain.your-domain.example.com |
Does it support the plus + symbol for Gmail aliases
Yes, absolutely.
Does it support sub-domains
Yes, absolutely. Instead of using "@", ".", or blank as the name/host/alias, you just use the sub-domain name as the value instead.
If you want foo.your-domain.your-domain.your-domain.your-domain.example.com to forward emails, then enter foo as the name/host/alias value in your DNS settings (for both MX and TXT records).
Does this forward my email's headers
Yes, absolutely.
Is this well-tested
Yes, it has tests written with ava and also has code coverage.
Do you pass along SMTP response messages and codes
Yes, absolutely. For example if you're sending an email to hello@your-domain.your-domain.your-domain.your-domain.example.com and it's registered to forward to user@gmail.com, then the SMTP response message and code from the "gmail.com" SMTP server will be returned instead of the proxy server at "mx1.forwardemail.net" or "mx2.forwardemail.net".
How do you prevent spammers and ensure good email forwarding reputation
See our sections on How does your email forwarding system work, How do you handle email delivery issues, and How do you handle your IP addresses becoming blocked above.
How do you perform DNS lookups on domain names
We created an open-source software project 🍊 Tangerine and use it for DNS lookups. The default DNS servers used are 1.1.1.1 and 1.0.0.1, and DNS queries are through DNS over HTTPS ("DoH") at the application layer.
🍊 Tangerine uses CloudFlare's privacy-first consumer DNS service by default.
Account and Billing
Do you offer a money back guarantee on paid plans
Yes! Automatic refunds occur when you upgrade, downgrade, or cancel your account within 30-days from when your plan first started. This only applies for first-time customers.
If I switch plans do you pro-rate and refund the difference
We do not pro-rate nor refund the difference when you switch plans. Instead we convert the remaining duration from your existing plan's expiration date into the closest relative duration for your new plan (rounded down by month).
Note that if you upgrade or downgrade between paid plans within a 30-day window since first starting a paid plan, then we will automatically refund the full amount from your existing plan.
Can I just use this email forwarding service as a "fallback" or "fallover" MX server
No, it is not recommended, as you can only use one mail exchange server at a time. Fallbacks are usually never retried due to priority misconfigurations and mail servers not respecting MX exchange priority checking.
Can I disable specific aliases
Yes, simply edit your DNS TXT record and prefix the alias with either one, two, or three exclamation marks (see below).
Note that you should preserve the ":" mapping, as this is required if you ever decide to toggle this off (and it's also used for importing if you upgrade to one of our paid plans).
For quiet reject (appears to sender as if the message was sent successfully, but actually goes nowhere) (status code 250): If you prefix an alias with "!" (single exclamation mark) then it will return a successful status code of 250 to senders attempting to send to this address, but the emails themselves will go nowhere (e.g. a blackhole or /dev/null).
For soft reject (status code 421): If you prefix an alias with "!!" (double exclamation mark) then it will return a soft error status code of 421 to senders attempting to send to this address, and the emails will often be retried for up to 5 days before rejection and bounce.
For hard reject (status code 550): If you prefix an alias with "!!!" (triple exclamation mark) then it will return a permanent error status code of 550 to senders attempting to send to this address and the emails will be rejected and bounce.
For example, if I want all emails that go to alias@your-domain.your-domain.your-domain.your-domain.example.com to stop flowing through to user@gmail.com and get rejected and bounce (e.g. use three exclamation marks):
| Name/Host/Alias | TTL | Type | Answer/Value |
|---|---|---|---|
| "@", ".", or blank | 3600 | TXT | forward-email=!!!alias:user@gmail.com |
| Name/Host/Alias | TTL | Type | Answer/Value |
|---|---|---|---|
| "@", ".", or blank | 3600 | TXT | forward-email=!!!alias:nobody@forwardemail.net |
| Name/Host/Alias | TTL | Type | Answer/Value |
|---|---|---|---|
| "@", ".", or blank | 3600 | TXT | forward-email=!!!alias |
Can I forward emails to multiple recipients
Yes, absolutely. Just specify multiple recipients in your TXT records.
For example, if I want an email that goes to hello@your-domain.your-domain.your-domain.your-domain.example.com to get forwarded to user+a@gmail.com and user+b@gmail.com, then my TXT record would look like this:
| Name/Host/Alias | TTL | Type | Answer/Value |
|---|---|---|---|
| "@", ".", or blank | 3600 | TXT | forward-email=hello:user+a@gmail.com,hello:user+b@gmail.com |
Or, you could specify them in two separate lines, such as this:
| Name/Host/Alias | TTL | Type | Answer/Value |
|---|---|---|---|
| "@", ".", or blank | 3600 | TXT | forward-email=hello:user+a@gmail.com |
| "@", ".", or blank | 3600 | TXT | forward-email=hello:user+b@gmail.com |
It's up to you!
Can I have multiple global catch-all recipients
Yes, you can. Just specify multiple global catch-all recipients in your TXT records.
For example, if I want every email that goes to *@your-domain.your-domain.your-domain.your-domain.example.com (the asterisk meaning its a wildcard aka catch-all) to get forwarded to user+a@gmail.com and user+b@gmail.com, then my TXT record would look like this:
| Name/Host/Alias | TTL | Type | Answer/Value |
|---|---|---|---|
| "@", ".", or blank | 3600 | TXT | forward-email=user+a@gmail.com,user+b@gmail.com |
Or, you could specify them in two separate lines, such as this:
| Name/Host/Alias | TTL | Type | Answer/Value |
|---|---|---|---|
| "@", ".", or blank | 3600 | TXT | forward-email=user+a@gmail.com |
| @, ".", or blank | 3600 | TXT | forward-email=user+b@gmail.com |
It's up to you!
Is there a maximum limit on the number of email addresses I can forward to per alias
Yes, the default limit is 10. This does NOT mean that you can only have 10 aliases on your domain name. You can have as many aliases as you want (an unlimited amount). It means that you can only forward one alias to 10 unique email addresses. You could have hello:user+1@gmail.com, hello:user+2@gmail.com, hello:user+3@gmail.com, … (from 1-10) – and any emails to hello@your-domain.your-domain.your-domain.your-domain.example.com would get forwarded to user+1@gmail.com, user+2@gmail.com, user+3@gmail.com, … (from 1-10).
Can I recursively forward emails
Yes, you can, however you still must adhere to the maximum limit. If you have hello:linus@your-domain.your-domain.your-domain.your-domain.example.com and linus:user@gmail.com, then emails to hello@your-domain.your-domain.your-domain.your-domain.example.com would get forwarded to linus@your-domain.your-domain.your-domain.your-domain.example.com and user@gmail.com. Note that an error will be thrown if you attempt to recursively forward emails beyond the maximum limit.
Can people unregister or register my email forwarding without my permission
We use MX and TXT record verification, therefore if you add this service's respective MX and TXT records, then you're registered. If you remove them, then you're unregistered. You have ownership of your domain and DNS management, so if someone has access to that then that's a problem.
How is it free
Forward Email offers a free tier through a combination of open-source development, efficient infrastructure, and optional paid plans that support the service.
Our free tier is supported by:
-
Open Source Development: Our codebase is open source, allowing community contributions and transparent operation.
-
Efficient Infrastructure: We've optimized our systems to handle email forwarding with minimal resources.
-
Paid Premium Plans: Users who need additional features like SMTP sending, IMAP receiving, or enhanced privacy options subscribe to our paid plans.
-
Reasonable Usage Limits: The free tier has fair usage policies to prevent abuse.
Note
We're committed to keeping basic email forwarding free while offering premium features for users with more advanced needs.
Tip
If you find our service valuable, consider upgrading to a paid plan to support ongoing development and maintenance.
What is the max email size limit
We default to a 50MB size limit, which includes content, headers, and attachments. Note that services such as Gmail and Outlook allow only 25MB size limit, and if you exceed the limit when sending to addresses at those providers you will receive an error message.
An error with the proper response code is returned if the file size limit is exceeded.
Do you store logs of emails
No, we do not write to disk or store logs – with the exception of errors and outbound SMTP (see our Privacy Policy).
Everything is done in-memory and our source code is on GitHub.
Do you store error logs
Yes. You can access error logs under My Account → Logs or My Account → Domains.
As of February 2023, we store error logs for 4xx and 5xx SMTP response codes for a period of 7 days – which contain the SMTP error, envelope, and email headers (we do not store the email body nor attachments).
Error logs allow you to check for missing important emails and mitigate spam false positives for your domains. They are also a great resource for debugging issues with email webhooks (since the error logs contain the webhook endpoint response).
Error logs for rate limiting and greylisting are not accessible since the connection ends early (e.g. before RCPT TO and MAIL FROM commands can be transmitted).
See our Privacy Policy for more insight.
Do you read my emails
No, absolutely not. See our Privacy Policy.
Many other email forwarding services store and could potentially read your email. There is no reason why forwarded emails need to be stored to disk storage – and therefore we architected the first open-source solution that does it all in-memory.
We believe you should have a right to privacy and we strictly respect it. The code that is deployed to the server is open-source software on GitHub for transparency and to build trust.
Can I "send mail as" in Gmail with this
Yes! As of October 2, 2018 we have added this feature. See How to Send Mail As using Gmail above!
You should also set the SPF record for Gmail in your DNS configuration TXT record.
include:_spf.google.com to your SPF TXT record, for example:
v=spf1 a include:spf.forwardemail.net include:_spf.google.com -all
Can I "send mail as" in Outlook with this
Yes! As of October 2, 2018 we have added this feature. Simply view these two links from Microsoft below:
- https://support.office.com/en-us/article/add-or-remove-an-email-alias-in-outlook-com-459b1989-356d-40fa-a689-8f285b13f1f2
- https://support.office.com/en-us/article/send-email-from-a-different-address-in-outlook-com-ccba89cb-141c-4a36-8c56-6d16a8556d2e
You should also set the SPF record for Outlook in your DNS configuration TXT record.
include:spf.protection.outlook.com to your SPF TXT record, for example:
v=spf1 a include:spf.forwardemail.net include:spf.protection.outlook.com -all
Can I "send mail as" in Apple Mail and iCloud Mail with this
If you are a subscriber to iCloud+, you can use a custom domain. Our service is also compatible with Apple Mail.
Please see https://support.apple.com/en-us/102540 for more information.
Can I forward unlimited emails with this
Yes, however "relatively unknown" senders are rate limited to 100 connections per hour per hostname or IP. See the section on Rate Limiting and Greylisting above.
By "relatively unknown", we mean senders that do not appear in the allowlist.
If this limit is exceeded we send a 421 response code which tells the senders mail server to retry again later.
Do you offer unlimited domains for one price
Yes. Regardless of which plan you are on, you will pay only one monthly rate – which covers all of your domains.
Which payment methods do you accept
Forward Email accepts the following one-time or monthly/quarterly/yearly payment methods:
- Credit/Debit Cards/Bank Transfers: Visa, Mastercard, American Express, Discover, JCB, Diners Club, etc.
- PayPal: Connect your PayPal account for easy payments
- Cryptocurrency: We accept payments via Stripe's stablecoin payments on Ethereum, Polygon, and Solana networks
Note
We store limited payment information on our servers, which only includes payment identifiers and references to Stripe and PayPal transaction, customer, subscription, and payment ID's.
Tip
For maximum privacy, consider using cryptocurrency payments.
All payments are processed securely through Stripe or PayPal. Your payment details are never stored on our servers.
Additional Resources
Tip
Our articles below are regularly updated with new guides, tips, and technical information. Check back often for the latest content.